How to Block Employees From Accessing Websites (Step-by-Step)
Employees shouldn't have access to all websites at all times of the day. Learn how to block access in this guide.

As an employer or manager, you've probably noticed staff browsing Facebook during work hours, or maybe you've discovered someone streaming Netflix when they should be finishing that quarterly report.
A few years ago, a U.S. government employee visited 9,000 inappropriate websites in under seven months, using their work computer to access adult content linked to Russian pages that contained malware.
This person averaged 79 inappropriate sites every business day and connected an unauthorized USB drive and personal phone to their work computer, which got infected.
That's an extreme case, but it shows why learning how to block employees from accessing websites matters. You're trying to protect company data, maintain network security, and avoid legal problems. This guide shows you how to control internet access effectively.

Reasons for Controlling Internet Access
Restricting internet access addresses clear operational risks. It also protects your bottom line since unmonitored browsing impacts business and employee productivity, network security, and legal standing.
Consider, for example, that significant time spent on non-work sites has a direct impact on your team's output. The key reasons companies limit internet access or restrict access entirely include:
- Productivity Losses: Distracting websites divert employees’ attention from critical business operations and directly impact business productivity.
- Legal Compliance: HIPAA requirements for healthcare, CIPA standards for schools, and copyright laws that prevent unauthorized downloads from torrent sites.
- Professional Environment: About 51% of employees working from home admit to browsing adult content on work-used devices, according to a Kaspersky survey. Companies block websites with adult content to maintain professionalism and protect all employees.
- Security Threats: When employees visit unvetted or harmful websites, they can expose your network to online threats like ransomware, malware, and phishing attacks.
- Bandwidth Management: Streaming sites can use up to 7GB per hour for 4K content, and 84% of Gen Z employees admit to streaming at work, slowing business-critical applications.
Building Your Policy for Blocking Unwanted Websites
You can't block access to everything, and you shouldn't try. A good internet access policy targets specific categories and helps you block specific websites or services that cause the most problems, while supporting legitimate work needs. Let’s look at some categories and how Control D can help you manage access:
Social Media
When you create a Control D account and go to your profile, you have two primary methods for blocking social media, plus a custom option.
Block Specific Platforms
- Navigate to Services > Social. Here, you will find a list of 57 social media platforms.
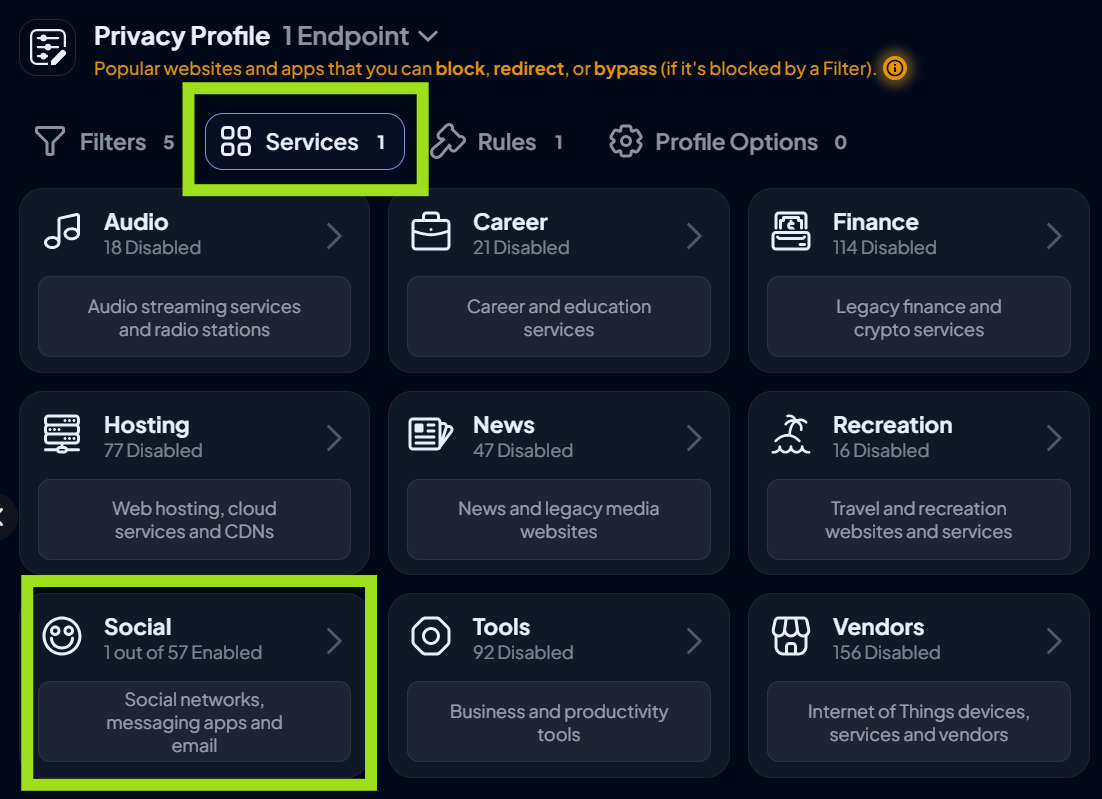
- Toggle on any service you wish to block.
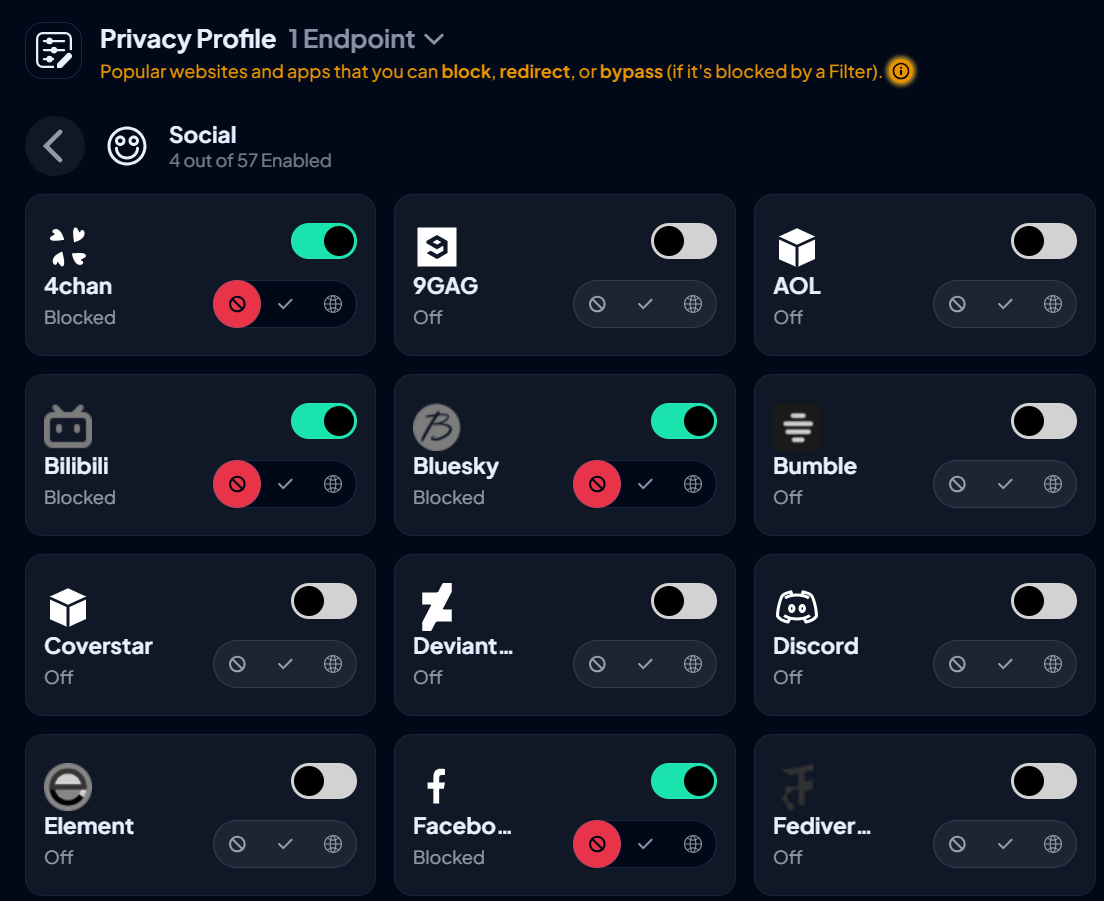
- This action will stop access to both websites and applications.
Block the Entire Category
- For a comprehensive block, go to Filters > Social and set the main toggle to Blocked.
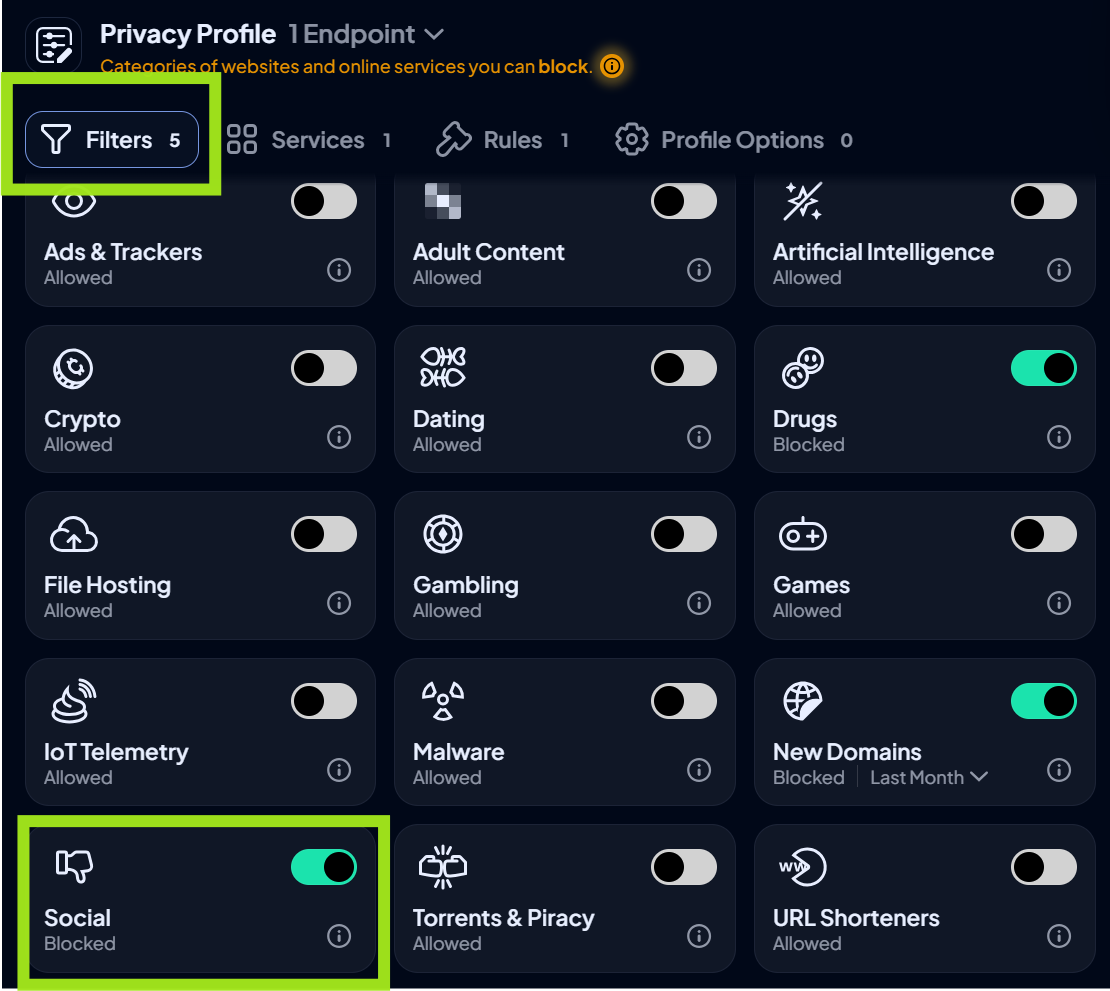
- This will restrict access to all services classified as social media.
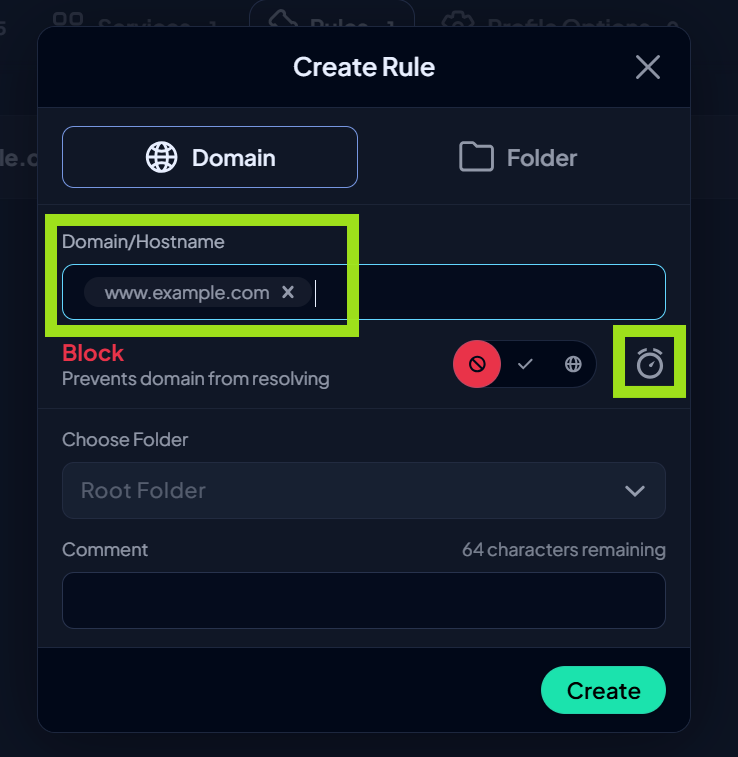
Create Custom Rules
- If a platform you use is not on the default list, you can block it directly. Locate Rules and click the + sign.
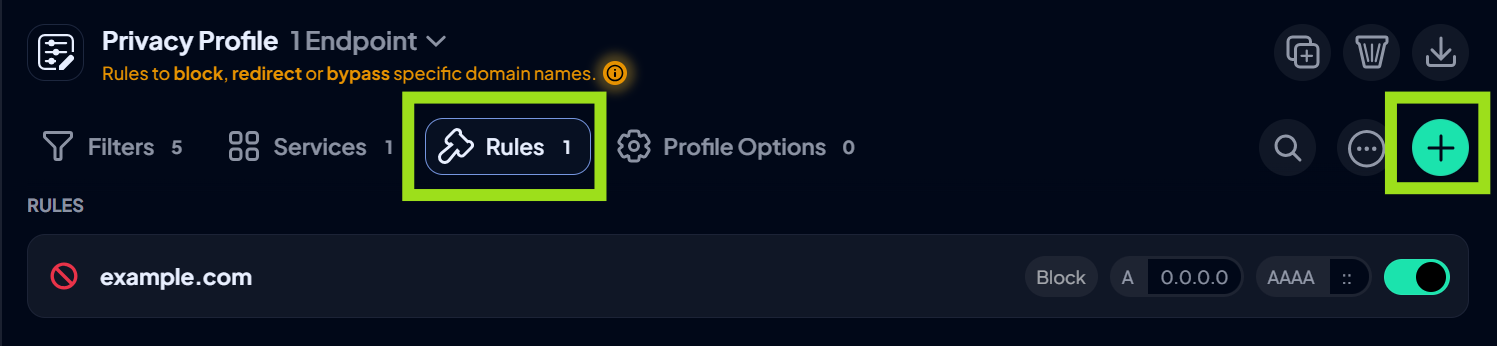
- Add the domain you want to block, and either click create or set a schedule if you only want the block active for a certain time on specific days. Click Create.
Streaming and Entertainment
Streaming services can slow your entire network when several people are watching simultaneously. With Control D, you can block access to a specific streaming service or set up a custom rule by following these steps:
- Navigate to Services > Video. Here, you will see a list of 314 streaming services you can block.
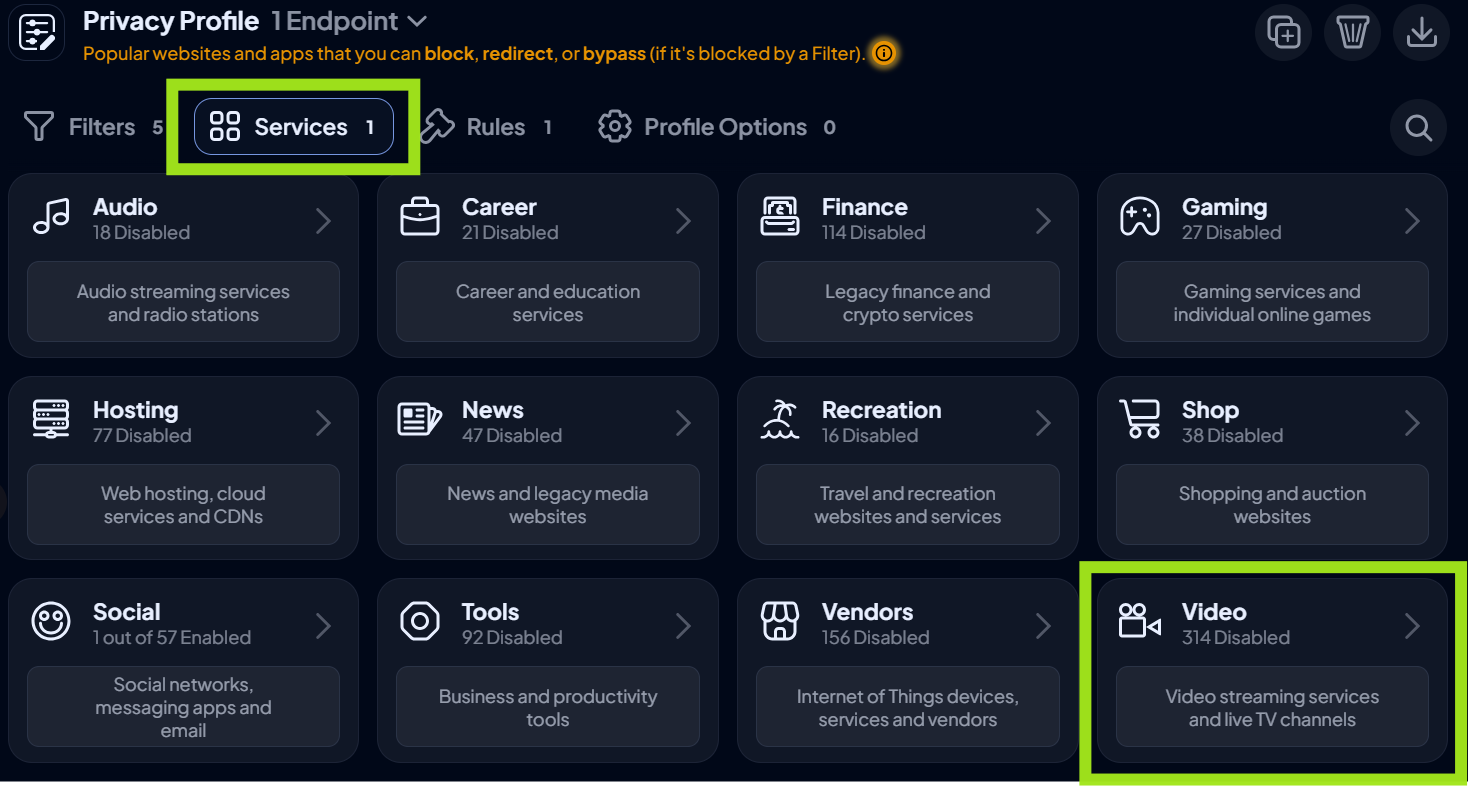
- Toggle on any (or all) of the services you want to block.
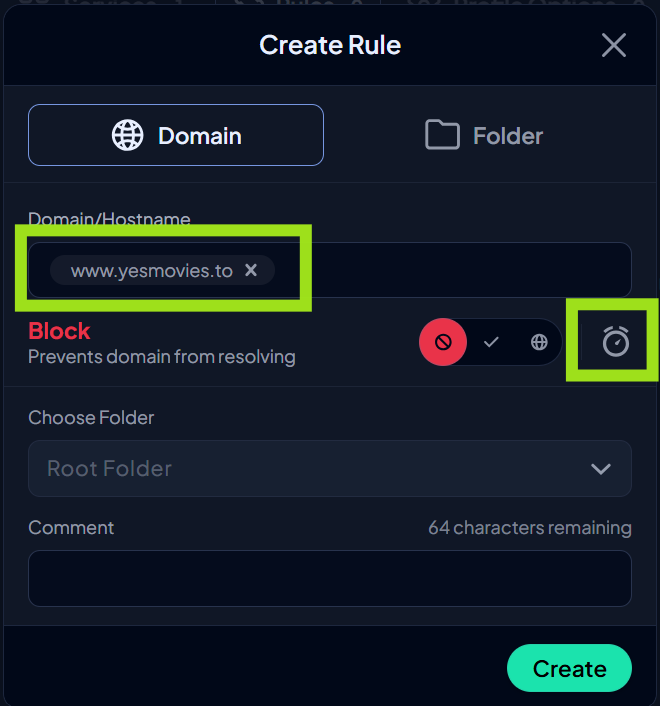
- To create a custom rule, go to Rules, click the + sign, and add the domain URL of the streaming service you want to block. Optional: Set an expiration date or schedule for your block.
Time-Wasting Sites and High Risk Content
You can apply the same steps above to manage any sites that affect staff productivity or pose a risk for your network. We recommend separating these sites into two groups: High-risk content and productivity and time-wasting sites.
High-risk content, such as phishing and malware sites, adult content, gambling sites, and torrenting and illicit file-sharing platforms, must be completely blocked. Use the Filters function to block these entire categories. This is the most effective way to protect your network and sensitive client data from threats.
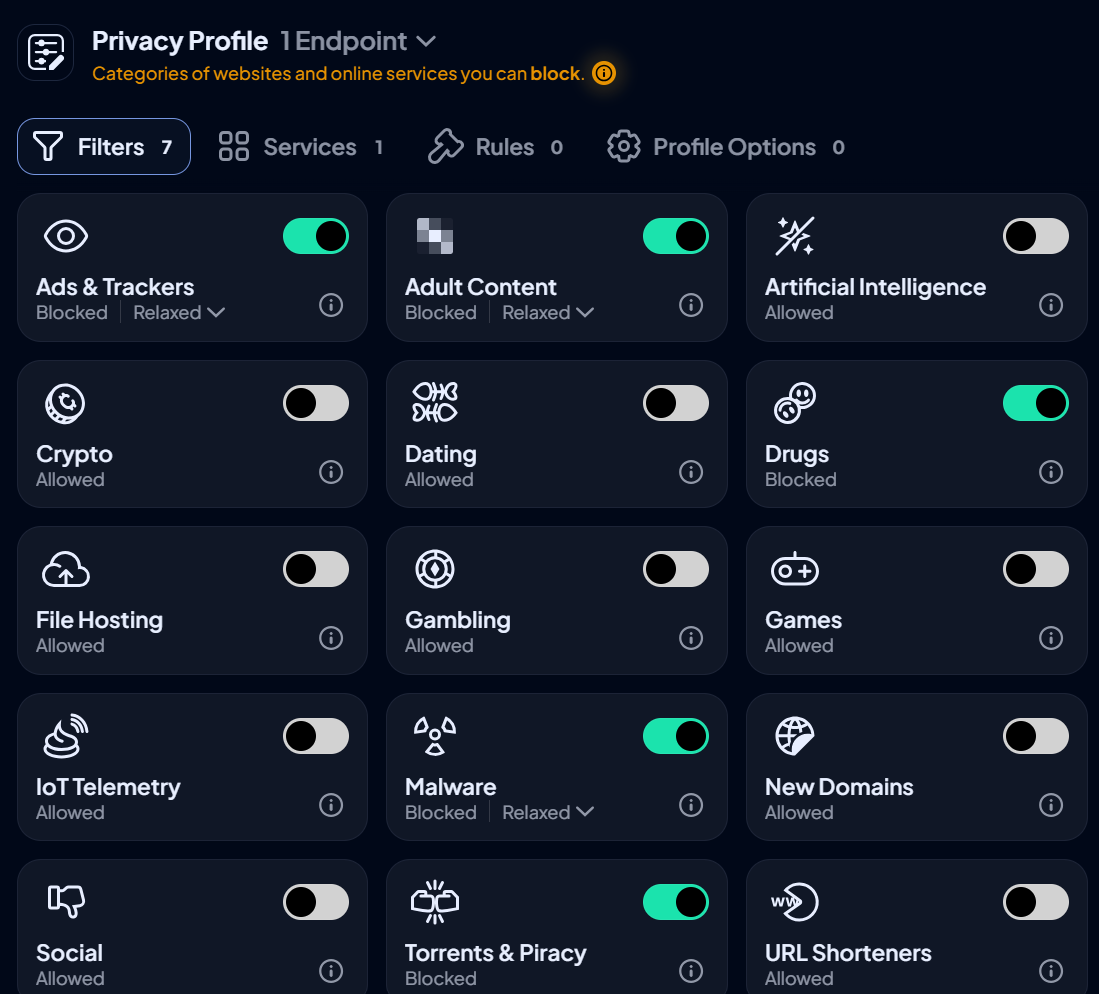
For productivity and time-wasting sites, you can apply a more flexible strategy. For example, your firm may not need to block all shopping sites, but may want to manage specific platforms or limit access with time-based blocks. For example, you can grant access to shopping sites during lunch hour. Add Custom Rules to block any sites that are not on the default lists.
Common Methods for Blocking Websites
You have several technical options for implementing internet access policies. Each method has different strengths for blocking websites effectively.
DNS Filtering
DNS filtering intercepts domain name lookups before they resolve to IP addresses. When an employee types a blocked website into the search bar, the DNS filter prevents the connection. This is one of the most effective methods to block access to unwanted websites. That said, DNS filtering can't block specific pages within a website; it can only block entire domains. You manage access at the domain level rather than individual web pages.
Key benefits of DNS filtering:
- Works at the network level, automatically protecting all devices without installing software on each one.
- Blocks sites before any data transfers occur.
- No HTTPS decryption is required, which improves performance.
- Lighter IT overhead.
- Protects remote employees when devices are configured to use the organization’s DNS resolvers.
- Less user circumvention.
Cloud-based DNS filtering is a cost-effective option. Control D’s solution includes management dashboards that let you adjust policies, view reports, and monitor blocked attempts. These comprehensive solutions support work in Active Directory environments and SSO for user identity.
Network Hardware
Business-grade routers and firewalls can block employees from certain websites at the network edge.
Routers work well for small offices that don't need sophisticated filtering. It's straightforward to set up, blocked sites are added through the admin panel, and it doesn't require a subscription.
The downside is manual management and a lack of granular control; most routers offer limited categories, and managing rules for different users can be clunky.
Firewalls offer more granular control than basic routers. You can block specific IP addresses, domain ranges, or traffic patterns. And they work well combined with other methods to create layered network security.
They can be hardware appliances in your server room or cloud-based services. The primary drawbacks are their cost and complexity, often requiring a steep learning curve and dedicated IT management.
Endpoint Software
Web filtering software installs on individual computers and controls what each device can access. This works for remote employees whose devices don't always connect to your internal network. Endpoint solutions offer:
- Category-based blocking with customizable policies for different user groups.
- Time-based rules that block distracting websites during work hours.
- Role-based policies supporting user permissions through Active Directory.
- Mobile Device Management (MDM) for smartphones and tablets.
Note: With modern DNS solutions like Control D, you can easily deploy protection to thousands of remote devices at scale using RMM or MDM tools, ensuring consistent policy enforcement wherever your staff are located – without complicated installation steps for each user.
Why Standard Web Filtering Fails: Countering Modern Evasion Tactics
Basic website blocking stops casual browsing but falls short against determined users who want to bypass internet restrictions and access blocked content.
Encrypted DNS (DoH/DoT)
DNS over HTTPS (DoH) and DNS over TLS (DoT) encrypt DNS queries, preventing traditional DNS filters from seeing which sites employees request. You can counter these tactics by:
- Disabling DoH through Group Policy settings in Windows environments.
- Configuring firewalls to block connections to known DoH servers at ports 443 and 853.
- Using modern DNS filtering services that maintain up-to-date blocks on known encrypted DNS endpoints and surface bypass attempts for review.
VPNs and Proxies
Proxy websites and VPN services route traffic through external servers, hiding the true destination. Your filter only sees the proxy or VPN endpoint, not the blocked site behind it. You can stop this by:
- Maintaining updated lists of proxy domains and VPN provider IP addresses.
- Using web filtering services with databases of known proxies and VPNs.
- Deploying endpoint software that works independently of network connectivity.
Browser-Level DNS Settings
Modern browsers let users change DNS settings independently of system-wide settings. An employee can configure Chrome or Firefox to use public resolvers like 8.8.8.8 or 1.1.1.1. Prevention methods include:
- Using endpoint software that controls browser settings through policies.
- Blocking outbound DNS traffic to external resolvers at your firewall level.
- Configuring Group Policy settings to prevent DNS changes.
Mapping Your Controls by Layer
Effective blocking requires controls at multiple layers:
- Endpoint: Web filtering software enforces policies on individual devices regardless of network location. Controls browser settings and monitors all internet activity.
- Browser: Enterprise policies configure Chrome and Edge settings centrally through Group Policy for all Active Directory users.
- Network: DNS filtering, firewalls, and router settings block sites for all devices connected to your internal network. Provides broad coverage without configuring individual devices.
- Cloud (Secure Web Gateways, SWG / Cloud Access Security Brokers, CASB): Secure Web Gateways inspect all web traffic. Cloud Access Security Brokers control access to cloud applications. Both provide consistent protection for remote workers, office employees, and mobile users.
Beyond Blanket Blocks: Granular Control with Role-Based Internet Restrictions
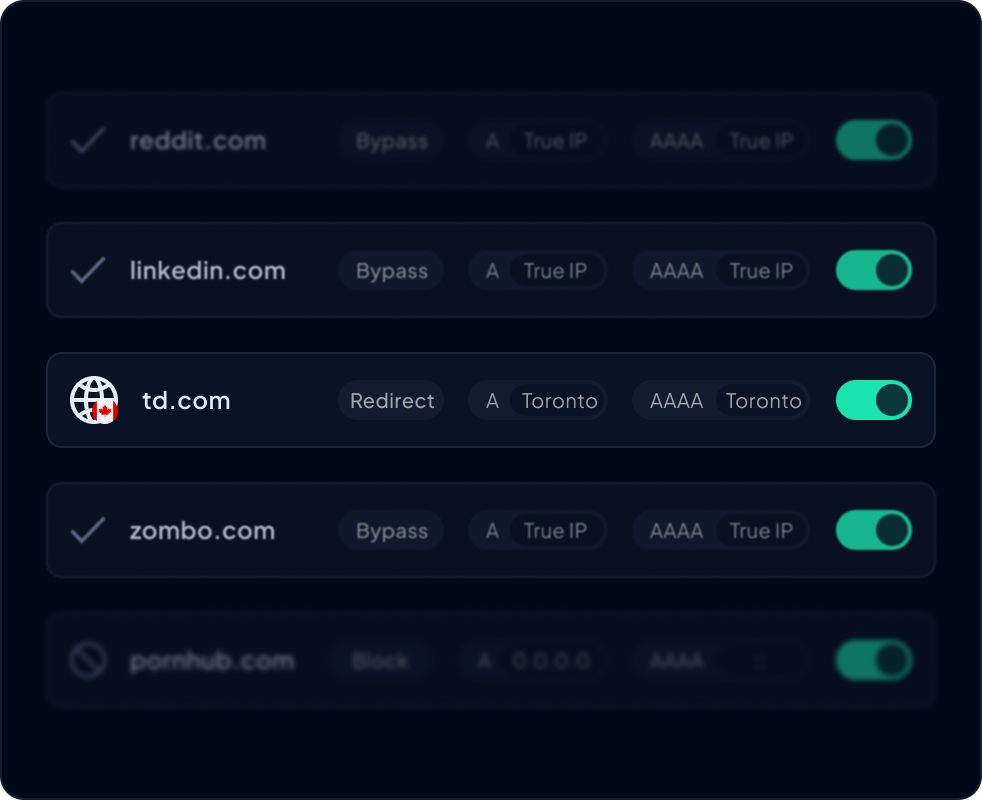
Different employees need different levels of web access. Your marketing team needs social media sites. Your IT staff needs access to technical forums and software repositories. Customer support might need YouTube to watch tutorial videos. One-size-fits-all policies don't work.
The solution is to create separate internet access policies for each department or job function. Instead of managing permissions for every individual, you use Active Directory integration. This lets you assign employees to existing groups (like “Sales” or “IT”) and apply a specific filtering policy to that entire group.
Examples of Role-Based Policies
Here is what this looks like in practice:
- Marketing Department: Full access to LinkedIn, X, and Facebook for managing company accounts and campaign research, including video streaming.
- Sales Teams: LinkedIn access for prospecting, but other social media sites and entertainment platforms are blocked.
- IT and Development: Access to Stack Overflow, GitHub, and technical documentation, including software repositories.
- Customer Support: YouTube access is limited to product tutorials and help videos.
- General Employees: Non-essential sites are blocked, while business-critical sites remain allowed.
Refine Policies with Time-Based Rules
You can add another layer of control by managing when sites are accessible. These time-based rules help maintain employee productivity without micromanagement. For instance, you can block access to distracting sites during core work hours, but automatically permit access during scheduled lunch breaks.
How Control D Can Help
You need DNS filtering that stops modern bypass tactics. Control D works at the network level, allowing you to create custom filtering rules called "Profiles." These Profiles are enforced on your network or specific devices ("Endpoints"), and every device or router configured to that Profile is protected within minutes.
Remote workers get the same protection as office employees. As long as remote workers’ devices are set up to use Control D's DNS resolvers, filtering and security apply wherever they are, regardless of location.
Implementation takes just a few simple steps. For office networks, log into your router, update your current DNS server addresses with Control D's, and filtering starts immediately.
For remote employees or a large number of devices, you can configure them at scale using your preferred RMM/MDM tool. Control D also integrates with Active Directory for automatic user group assignments and works seamlessly alongside your existing firewall and endpoint tools.
There's also a "VPN & DNS" Filter that blocks most known VPNs and DNS services used to bypass restrictions, and updates regularly to keep pace with new methods.
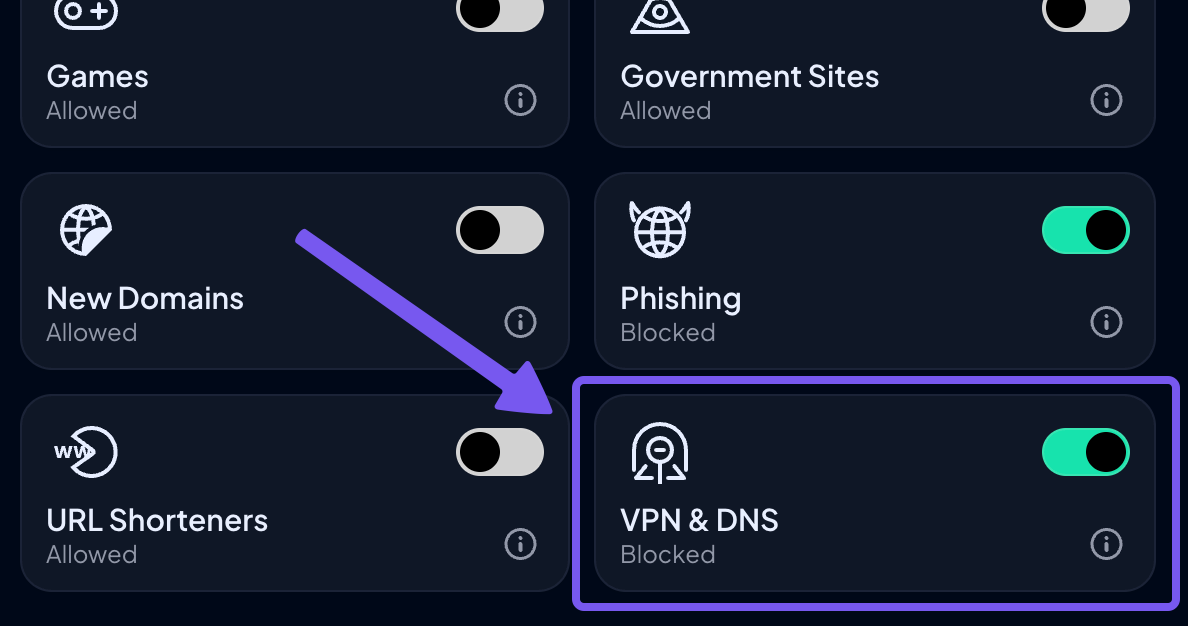
This “Profile” system allows for granular control. You can use broad “Filters” to block entire categories (like Gambling or Malware) while also using “Services” rules to block specific applications like TikTok or Steam, or create exceptions.
Plus, you can create separate Profiles for different users, and have multiple enforced Profiles. This means you can enforce a company-wide Profile that blocks things like Malware, Social Media, Phishing, etc., and then create a Profile specifically for your marketing team that allows access to a "Service" like LinkedIn, Facebook, or X.
This lets you tailor your filtering policies to specific users or specific teams, ensuring they have access to all the tools necessary for their role – no more, no less. You can also set time-based rules that automatically switch Profiles, blocking social media sites during work hours but allowing access during lunch breaks.
Read more: Want the full step-by-step setup process? Read our complete guide: How to Restrict Internet Access (Block Content): Step-by-Step Guide for detailed instructions on creating profiles, configuring endpoints, setting up schedules, and monitoring your network.
FAQs about Blocking Websites from Employees
How to Block Employees from Accessing Websites
Start with DNS filtering services like Control D for network-wide protection. Point your DNS settings to the filtering service and configure category blocks for gambling, adult, and torrent sites. Deploy Control D onto devices themselves to secure remote workers, and create department-specific rules via separate Profiles.
Can an Employer Legally Block Websites?
Yes, employers can legally block websites on company-owned devices and networks in most jurisdictions. Courts recognize that companies have a legitimate interest in controlling their equipment and internet connections. Notify employees through written internet access policies in employee handbooks and require a signed acknowledgment during onboarding.
Different rules apply to personal devices in BYOD environments. Some industries face specific regulations, such as HIPAA for healthcare or CIPA for schools.
How to Block Social Media Websites on Chrome?
For network-wide blocking, use DNS filtering services that block the social media category across all browsers and apps. For Windows business environments, configure proxy settings through the Group Policy Management Console to block social media domains.
This affects Chrome because it uses Windows proxy settings. For individual devices, point Chrome's DNS settings to Control D's server addresses, but remember that employees can bypass them by switching browsers. Create role-based exceptions for marketing teams needing social media access.
What is the Most Effective Method for Blocking Websites?
DNS filtering gives you the best effectiveness and performance balance, blocking websites before data transfers occur. It protects both on-premise devices and networks, and remote devices when configured correctly.


