What Is DNS Traffic?
DNS traffic refers to the network communication involving DNS (Domain Name System) queries and responses. Learn about common tools and implementation.

DNS traffic refers to the network communication involving DNS (Domain Name System) queries and responses. It occurs when a device requests the IP address of a domain name from a DNS server. The server replies with the corresponding IP, enabling the device to connect to the requested website or service.
The Basics of DNS
The internet is built on a series of numerical addresses, IP addresses, that identify every device and server connected to the global network. Unfortunately, for humans, remembering a string of numbers like 172.217.164.110 for Google’s IP address is cumbersome.
Instead, we rely on friendly, easy-to-remember domain names like “google.com” or “example.org.” The Domain Name System acts as a massive, decentralized directory that pairs these domain names with their corresponding IP addresses.
Every time you enter a URL into your browser, the DNS steps in behind the scenes to translate that domain into an IP address, enabling your browser to find and load the correct web page.
The Components and Workflow of DNS Traffic
To understand DNS traffic, consider the journey of a single DNS query. Suppose you type “www.example.com” into your browser. Your device first checks its local DNS cache to see if it already knows the corresponding IP address.
If not, it sends a DNS query to a DNS resolver—often your Internet Service Provider’s (ISP) DNS server or a public DNS resolver. The resolver in turn queries a hierarchy of DNS servers:
- Root Servers: These servers handle queries about top-level domains (TLDs) such as “.com” or “.org.”
- TLD Name Servers: They direct the query to the appropriate authoritative name server for the specific domain.
- Authoritative Name Servers: These are the final arbiters for a particular domain, holding DNS records that map domain names to IP addresses. They respond with the correct IP address.
Types of DNS Queries and Responses
Recursive Query
The DNS resolver does all the work for the client, querying multiple servers until it obtains a final answer. This often happens behind the scenes, so from the user’s perspective, a single query yields a result.
Iterative Query
Here, the DNS resolver might respond with a referral, directing the client to another server. The client continues this process until it reaches an authoritative answer.
Responses
Once the authoritative server returns the IP address, that response travels back through the chain to the user’s device. The result is then cached locally to speed up future requests.
Protocols and Security Considerations
By default, DNS queries typically use the User Datagram Protocol (UDP) on port 53 because UDP is fast and efficient for short queries and responses. Occasionally, DNS uses the Transmission Control Protocol (TCP) for larger responses or certain security measures.
In recent years, security enhancements have been introduced, such as DNS over HTTPS (DoH) and DNS over TLS (DoT), which encrypt DNS traffic to prevent eavesdropping or tampering.
What Is DNS Traffic Blocking?
DNS traffic blocking refers to any method that uses the DNS resolution process to prevent access to certain domain names or categories of websites. Instead of simply translating domain names to IP addresses, the DNS resolver or a specialized DNS filtering service can deliberately withhold the correct IP address or provide an alternative “blocked” address.
This ensures that when a device tries to connect to a prohibited domain, whether a known malicious site, a phishing URL, or a category of websites restricted by an organization, it cannot successfully resolve the domain. As a result, the user cannot load the associated webpage.
How DNS Traffic Blocking Works
The mechanism behind DNS traffic blocking is relatively straightforward. When a DNS query for a blocked domain arrives, the DNS server or filtering service checks its internal database (a blocklist, content filtering policy, or malware feed) to determine if the requested domain is allowed.
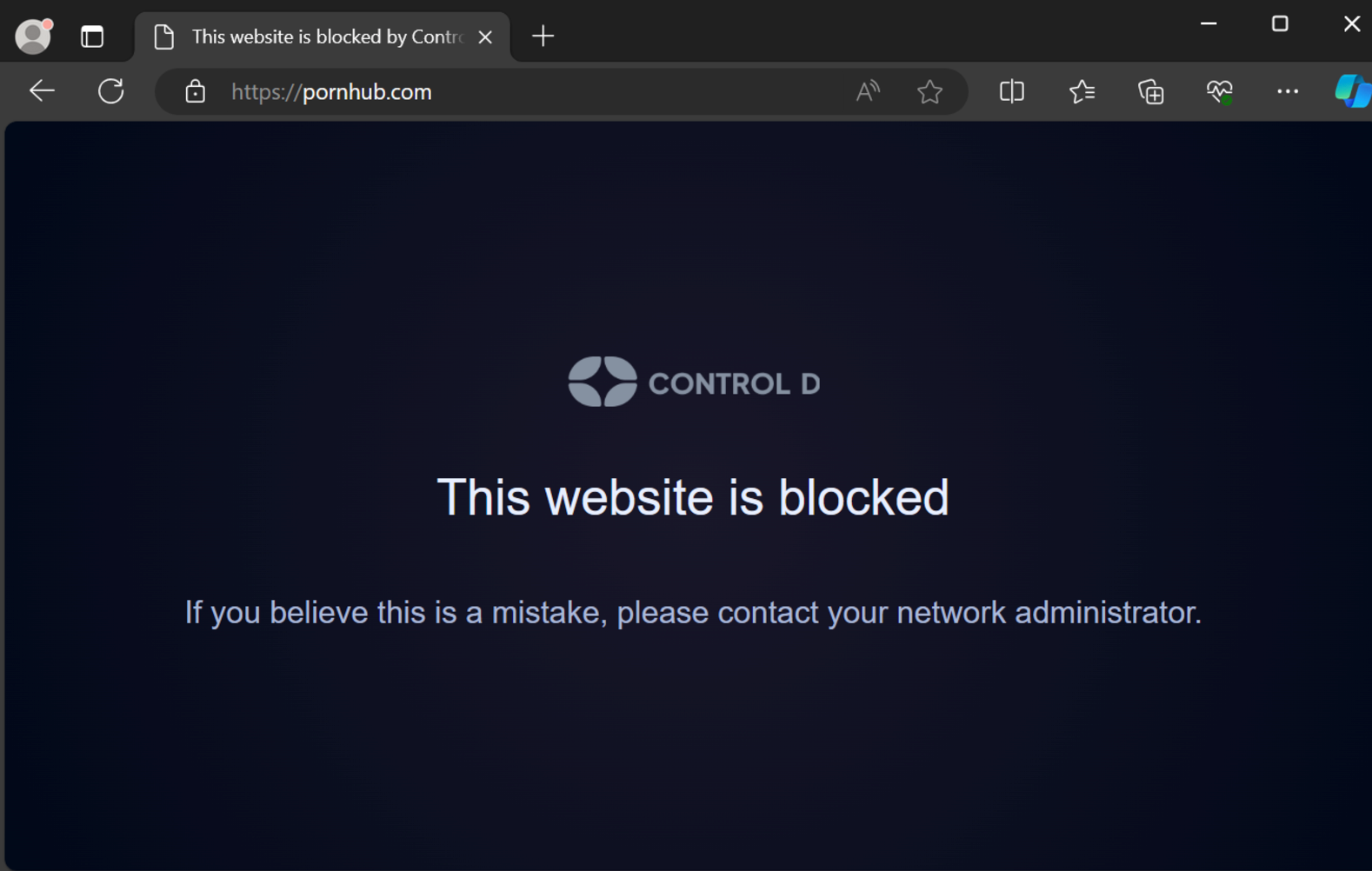
If it’s disallowed, the DNS resolver doesn’t return the correct IP address. Instead, it may respond with an IP address leading to a “blocked” page, a warning message, or simply return an error. This approach is often more efficient and user-friendly than traditional URL blocking methods, as it stops unwanted connections at the very start of the browsing process.
Common Tools and Implementations
A variety of DNS-based content filtering tools and services are available. Organizations and individuals may use:
- Enterprise DNS Filters: Solutions integrated into corporate networks and DNS infrastructure to enforce company-wide policies.
- Home DNS Filters: Services that let parents apply filters on home networks to restrict adult content or malicious websites.
- ISP-Level DNS Blocking: Some ISPs and countries implement DNS blocking at the network level to comply with legal requirements or protect users.
- Security Suites: Cybersecurity vendors often bundle DNS filtering into their threat prevention solutions, blocking known malicious domains before any connection occurs.
Why Should You Use DNS Traffic Blocking?
Enhancing Cybersecurity
DNS traffic blocking serves as a robust first line of defense. Because DNS queries occur before any data is exchanged with the target website, blocking suspicious domains at the DNS level prevents harmful connections from forming.
If a malicious link is clicked accidentally, the request is thwarted before the browser can load malicious code or prompt dangerous downloads. This proactive approach reduces the risk of data breaches, identity theft, and infiltration of corporate networks by bad actors.
Protecting User Privacy and Data
By selectively blocking known malicious or tracking domains, DNS traffic blocking can also contribute to better user privacy. Ad trackers and malicious scripts often rely on numerous third-party domains. When these domains are blocked at the DNS level, they never load.
As a result, your online footprint is smaller, fewer cookies are dropped on your system, and the ability of advertisers or cybercriminals to profile or track your activities diminishes.
Complying With Regulations and Policies
For organizations and educational institutions, DNS traffic blocking can be instrumental in complying with internal policies or external regulations. Companies that must uphold specific cybersecurity standards, data protection regulations, or industry-specific guidelines can use DNS-based filtering to prevent employees from visiting prohibited sites or interacting with domains that may compromise compliance. Schools and universities can similarly ensure students do not access harmful or distracting content.
Controlling Content and Improving Productivity
From a parental control standpoint, DNS traffic blocking helps ensure children have a safer online experience. Parents can block categories of adult content, gambling sites, or violent material without installing complicated software on each device.
Similarly, businesses can enhance productivity by blocking time-wasting sites, social media (if desired), or known security risks. The granular level of control offered by DNS filtering tools allows admins to tailor access according to their unique needs.
Reducing Bandwidth Waste and Improving Network Performance
When DNS blocking prevents certain types of content from loading—particularly heavy ads, unnecessary trackers, and malicious websites that might lead to large unsolicited downloads—it inherently contributes to more efficient use of network bandwidth. By eliminating these unwanted connections at the DNS level, the overall performance of a network can improve. This translates to faster load times for legitimate websites, reduced latency, and a smoother online experience for all users.
Examples of DNS Traffic Blocking
Businesses that want to protect its employees from accidentally visiting phishing sites can configure DNS blocking at the network level. Now, whenever an employee clicks a suspicious link in an email, the DNS query fails, and no harmful content is delivered. This simple yet effective measure prevents data theft, login credential compromise, and potential ransomware infections.
A family might use a consumer DNS filtering service to ensure their children don’t encounter adult content. By subscribing to a family-friendly DNS service and configuring it on their home router, they effortlessly enforce age-appropriate browsing without installing software on individual devices. This ensures a safer online environment for kids and greater peace of mind for parents.
A large enterprise with global branches can enforce consistent security policies. By deploying DNS-based filtering on their central DNS infrastructure, they ensure every employee, regardless of location, is protected from known malicious domains. If a new threat emerges in one region, updates to the DNS blacklist propagate network-wide, safeguarding the entire company at once.
Conclusion
To sum up, DNS traffic refers to the network communication exchanged during the resolution of domain names into IP addresses. When a user types a web address into a browser, the browser sends a DNS query to a DNS resolver. The resolver contacts authoritative name servers to find the corresponding IP address. This process involves multiple queries and responses traversing the internet, constituting DNS traffic.
In an increasingly complex internet landscape, understanding DNS traffic and the value of DNS traffic blocking is critical. DNS traffic is the invisible lifeblood of the internet—without it, we’d be forced to navigate by IP address, a cumbersome and error-prone process.
DNS traffic blocking offers a broad spectrum of advantages, from preventing malware infections and phishing attacks to ensuring compliance, boosting productivity, and protecting user privacy.
It operates at the earliest stage of a web connection, ensuring unwanted or dangerous destinations are never reached. With easy deployment, scalable solutions, and synergy with other security measures, DNS traffic blocking stands as a smart, proactive, and resource-efficient strategy to make the internet a safer, more controlled environment for everyone.

