Best Perimeter 81 Alternatives for DNS Security and Secure Remote Access
This guide compares alternatives to Perimeter 81 across four areas: SASE and Zero Trust Network Access (ZTNA) platforms, DNS-based security, self-hosted VPNs, and lightweight VPN services

If Perimeter 81 is starting to feel heavier and more expensive than the secure remote access you actually need, you’re not the only one. Many organizations outgrow their pricing and agent overhead long before they outgrow basic remote access VPN and network security needs.
This guide compares alternatives to Perimeter 81 across four areas: SASE and Zero Trust Network Access (ZTNA) platforms, DNS-based security, self-hosted VPNs, and lightweight VPN services. You’ll see how each option handles secure access to company resources, secure web gateway functions, data protection, and threat protection for remote workers and local networks.
To achieve this, we break down key features, where each solution fits, and how a DNS layer such as Control D can sit alongside SASE tools, legacy VPNs, and newer Zero Trust access (ZTA) platforms to give you more control over access and security policies.
Best Perimeter 81 Alternatives by Category and How We Chose Them
For this guide, we looked at vendor documentation, public reviews, and where these tools would typically appear in real network access stacks. Then we grouped them by what they actually do, rather than just by rating or name, so you can match them to your main use case.
Here’s our top choices for Perimeter 81 alternatives at a glance:
| Category | Recommended Perimeter 81 alternative | Why it stands out |
|---|---|---|
| Best overall Perimeter 81 alternative for a full SASE-style stack | Zscaler Internet Access | Cloud security service with a secure web gateway, firewall as a service, data loss prevention, and threat protection for large enterprises with many sites and remote users. |
| Best SASE alternative for cloud-first teams | Cloudflare Zero Trust | Zero trust security and cloud native SASE platform that combines DNS filtering, ZTNA, secure web gateway, and network connectivity on a global public infrastructure with many global POPs. |
| Best DNS-based alternative or complement for safer internet access | Control D | DNS filtering with content filtering, category and service-based rules, traffic redirection, and granular access controls that work with many VPN and ZTNA tools. |
| Best app-level Zero Trust option | Twingate | A ZTNA platform that focuses on ZTA to individual apps instead of broad network ranges, and that fits distributed teams and modern trust architecture patterns. |
| Best lightweight VPN for small teams | Windscribe (ScribeForce) | Team VPN accounts with central billing that give small organizations a low-cost VPN presence and pair well with a separate DNS layer for security policies. |
| Best self-hosted VPN option | OpenVPN Access Server | Self-hosted VPN servers that live in your own cloud environments or local networks and give you control over IP addresses, routing, and integration. |
Why are Perimeter 81 Users Looking at Alternatives
Perimeter 81 is a fast and flexible network access and Zero Trust security solution. It uses encrypted tunnels, ZTNA, and identity-based policies to control access between users and company resources.
It also offers secure web gateway features, cloud firewall functions, and seamless integrations with identity providers. The platform gives organizations a comprehensive suite of security features to protect against cyber threats.
For many teams, this single vendor approach is attractive. They get one cybersecurity platform to manage access, apply security policies, and run threat protection for remote workers, office users, and contractors. It can help them deploy Zero Trust architecture concepts, such as least-privileged access and zero trust access, without building everything from scratch. That said, users report common sticking points that are making them look to alternatives:
- Per-user pricing and minimum seat counts that raise costs as more users join.
- Extra charges for gateways or specific features, and advanced threat protection options
- Less flexible logging and web filtering capabilities compared to alternatives.
- A feeling that the platform is more than some organizations need when local networks and smaller sites have simple requirements.
- The need to separate DNS security and content filtering from the main SASE or VPN layer.
Given these sticking points, evaluating whether a different mix of network access and security tools would work better is often the next step. Some want a different Zero Trust security platform. Others want a DNS layer that stays independent from SASE. Others want a simpler remote-access VPN stack and use DNS tools to provide malware protection and domain-level threat intelligence.
If you fall into that latter group, or simply want to decouple security policy from connectivity, starting with the DNS layer is the most strategic move.
DNS-Based Alternatives For Internet Access Security
DNS security tools sit at the first step of many connections. They receive DNS queries from users and devices, check them against threat intel, security policies, and content filtering rules, then allow, block, or redirect traffic.
While DNS tools don’t replace ZTNA for private apps, they can handle much of the internet access security that some teams currently route through Perimeter 81.
Control D: Granular DNS Security and Traffic Control
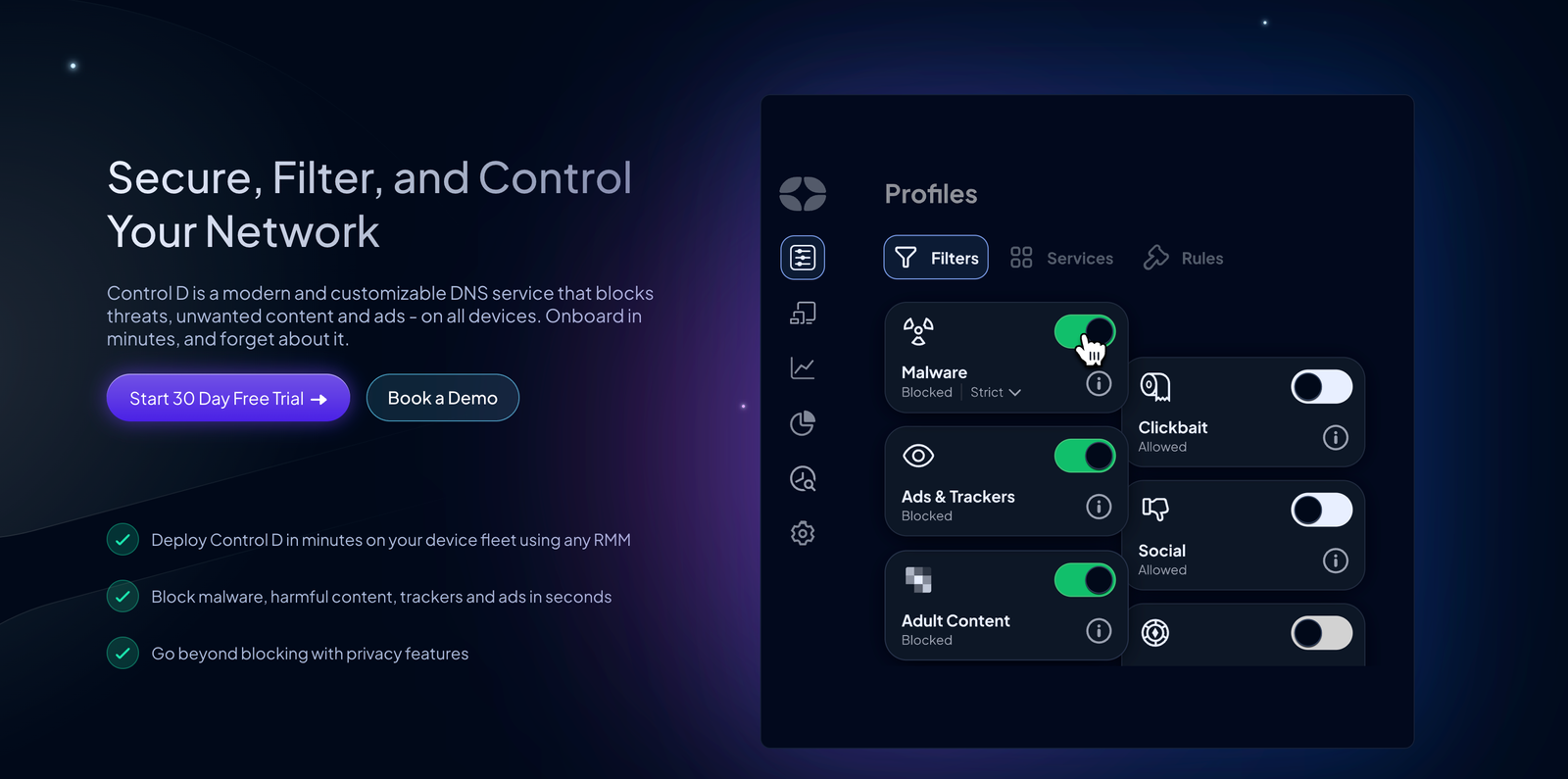
Control D is a DNS-based cybersecurity solution that focuses on content filtering, security filtering, and traffic steering. It lets organizations define DNS policies for networks, roaming users, and specific devices from one console.
Key features include:
- Security and content categories that help with malware protection, phishing defence, and acceptable use.
- Service-based rules for popular web apps and SaaS applications.
- Custom domain rules to block, allow, or redirect traffic based on risk or business need.
- Data protection rules enforcement through domain level controls and logging.
- Granular access controls that let you scope policies by network, user, group, or device.
- Traffic redirection through many exit locations for VPN-style browsing and policy enforcement.
- DNS logs that support threat intel work, investigations, and compliance needs.
- Security for remote workers without forcing every packet through a full SASE tunnel.
Control D vs. Perimeter 81
- Control D starts at $2 per endpoint per month, significantly less than Perimeter 81's starting price of $8 per user per month, making it more cost-effective for teams and individuals.
- Control D gives you a specialized DNS security layer with threat and content categories, per-client rules, logging, and traffic redirection on a global anycast network. Perimeter 81 includes DNS and web filtering as part of a larger SASE stack, so Control D is better suited when you want independent DNS policies that are easy to combine with any VPN or ZTNA platform.
- Control D can route traffic through many exit locations, rotate IP addresses, and apply proxy-style redirection, so users can change apparent location and keep browsing activity separate from their real IP. Those features sit on top of its DNS filtering and work with any underlying VPN or access stack.

Where Perimeter 81 Wins
Perimeter 81 and other SASE platforms combine ZTNA, secure web gateway inspection, network access control, and inline data protection. They can be a better fit when an organization wants access control and inspection for a wide range of traffic, not just DNS.
Best For
Organizations that want a dedicated DNS security layer, either as a partial replacement for Perimeter 81’s web layer or as an independent DNS policy engine across several network access tools.
DNSFilter
DNSFilter is a cloud-based DNS security service for IT departments and service providers. Choosing between DNSFilter and Perimeter 81 depends heavily on whether your primary need is DNS security and content filtering or a comprehensive secure access solution with VPN and Zero Trust capabilities.
DNSFilter vs. Perimeter 81
- DNSFilter provides real-time DNS-based threat detection and domain-level content filtering, while Perimeter 81 offers broader SASE tools, including ThreatCloud AI and VPN-integrated DNS filtering.
- It’s ideal for network security via domain access control and malicious site blocking, unlike Perimeter 81's focus on Zero Trust access, FWaaS, and ZTNA.
- DNSFilter offers easy deployment without endpoint software via DNS changes; Perimeter 81 requires lightweight agents for full VPN/ZTNA enforcement.
Where Perimeter 81 Wins
DNSFilter is purely a DNS and web security layer; it doesn’t offer the private network access or ZTNA capabilities of Perimeter 81. If you need to let remote users access internal company servers or private cloud resources safely, DNSFilter cannot replace that connectivity layer.
Best For
Service providers and IT firms that want an MSP-friendly DNS filter that slots into their own support and reporting processes.
NextDNS

NextDNS is a privacy-focused DNS resolver that gives per-device profiles and detailed controls for tracking protection, security filtering, and logging. It’s popular among individuals and small teams who want strict control over privacy and DNS logging. That said, it lacks some of the advanced features needed for business use cases.
NextDNS vs. Perimeter 81
- NextDNS blocks malware/phishing at DNS level with custom lists; Perimeter 81 uses AI for threat detection, SIEM, and integrated DNS via gateways.
- It uses simple DNS changes, with no agents, while Perimeter 81 requires cloud gateways and endpoint agents for enforcement.
- Pricing for NextDNS Business starts at $19.90 per month for 50 users, compared to the Perimeter 81 business plan at $12 per user per month and $40 per month per gateway (minimum of 10 users required).
Where Perimeter 81 Wins
Perimeter 81 outshines NextDNS in enterprise-grade ZTNA, enabling secure, granular app access for remote teams with device posture checks and FWaaS, beyond NextDNS's DNS-only filtering.
It also excels in comprehensive SASE platform scalability, offering VPN, SIEM integration, SSO, and multi-tenant management for large organizations, unlike NextDNS's personal/SMB-focused DNS resolver.
Best For
Home networks and SMBs needing detailed analytics, real-time logs, and encrypted DNS (DoH/DoT) without agents or enterprise overhead.
Comparison Guide: Control D vs. NextDNS If you’re choosing between these two DNS layers, this guide details the specific differences in logging, proxy capabilities, and enterprise controls.
SASE and ZTNA Alternatives
While DNS security handles high-level filtering and threat blocking, it doesn’t replace the need for deep packet inspection or private encrypted tunnels. If your goal is to replace Perimeter 81 with a similar all-in-one platform that supports ZTNA, secure web gateways, and full traffic inspection, you should consider dedicated SASE suites.
These alternatives replicate Perimeter 81’s core architecture but offer different strengths in scaling, pricing, and cloud integration.
Zscaler Internet Access
Zscaler Internet Access is a cloud native secure web gateway and firewall service that sits between users and the internet. It offers inspection, data loss prevention, and advanced threat protection to reduce exposure to new threats.
Zscaler vs. Perimeter 81
- Zscaler offers enterprise-grade global PoPs and UEBA for large organizations. Perimeter 81 targets SMBs with simpler management.
- It provides advanced ATP, RBI, and analytics scoring. Perimeter 81 offers basic AI threats and DNS filtering.
- Zscaler includes native DLP with exact matching. Perimeter 81 lacks advanced DLP.
- The price for Zscaler is $72-$375 per user per year, while Perimeter 81 ranges from a free tier to $8-$16 per user per month.
- Zscaler uses proxy-based full inspection. Perimeter 81 employs an agent/gateway for quick setup.
Where Perimeter 81 Wins
Smaller organizations that care more about a low-cost remote access solution may find Zscaler more than they need. In those cases, Perimeter 81 or lighter VPN tools can be faster to deploy.
Best For
Zscaler suits complex, high-compliance environments needing comprehensive SSE/SASE.
Cloudflare Zero Trust
Cloudflare Zero Trust is a Zero Trust security and SASE service that runs on Cloudflare’s global public infrastructure. It combines DNS filtering, secure web gateway controls, ZTA to internal apps, and network connectivity so that organizations can route traffic through Cloudflare’s global POPs.
Cloudflare Zero Trust vs. Perimeter 81
- Feature set for Cloudflare Zero Trust spans ZTNA, Secure Web Gateway, Cloud Access Security Broker (CASB), data loss prevention (DLP), remote browser isolation, Magic WAN, and Magic Firewall, and Perimeter 81 offers ZTNA, Secure Web Gateway, CASB, FWaaS, VPN-style access, and a private backbone.
- Network reach and deep DNS/HTTP visibility are key strengths on the Cloudflare side, and Perimeter 81 leans on Check Point threat protection, mid-market fit, and clear SASE bundles.
- Teams already using Cloudflare DNS, CDN, or WAF and needing strong networking features often lean to Cloudflare Zero Trust, and mid-sized organizations that want a guided SASE/SSE product for remote and branch users often prefer Perimeter 81.
Where Perimeter 81 Wins
Organizations tied into other vendors, such as Check Point, Cato Networks, or Palo Alto Networks Prisma Cloud, may find closer ties to their existing stack if they move within those ecosystems instead of to Cloudflare.
Best For
Cloud-first teams that use Cloudflare today and want to add Zero Trust network security and secure access without piecing together several unrelated tools.
Further reading: To understand the key differences between Cloudflare’s global network speed and NextDNS’s granular privacy controls before you make a decision: NextDNS vs. Cloudflare.
NordLayer
NordLayer is a business-focused VPN and ZTNA service from the Nord Security group. It offers secure remote access, site-to-site networking, and network access control aimed at small and mid-sized organizations.
Nordlayer vs. Perimeter 81
- NordLayer is a business VPN and ZTA platform for small and mid-sized teams, while Perimeter 81 is a broader SASE/SSE service with secure remote access, web gateway, CASB, and firewall on a managed backbone.
- It’s usually added as a secure remote access and zero trust layer on top of existing networks and clouds, while Perimeter 81 replaces more of the stack as an all-in-one SASE fabric for offices, clouds, and remote users.
- NordLayer focuses on secure remote access features such as site-to-site tunnels, virtual gateways, malware and phishing protection, DNS filtering, and SSO with MFA, while Perimeter 81 extends this with a full secure web gateway, CASB, FWaaS, and SD-WAN-style connectivity on a private backbone.
Where Perimeter 81 Wins
Perimeter 81 is ahead anywhere you want full SASE + SD-WAN + Check Point-grade threat prevention as your main stack, not just a business VPN with Zero Trust.
Best For
Mid-market organizations that want ZTA and network access control in a package that feels lighter than heavy SASE suites.
Twingate
Twingate is a ZTA access platform that focuses on application access instead of broad network ranges.
Twingate vs. Perimeter 81
- Perimeter 81 starts at $8 per user/month (billed yearly), while Twingate offers lower entry pricing at $5 per user/month.
- Resources remain hidden behind software-defined perimeters with Twingate's default split tunneling, whereas Perimeter 81 publicly exposes network entry points that require manual split-tunnel configuration.
- Deployment alongside existing networks takes just 15 minutes for Twingate, but Perimeter 81 often needs extensive planning as a full WAN and remote access replacement.
Where Perimeter 81 Wins
Perimeter 81 outperforms Twingate in enterprise-scale integrations and advanced SASE features, such as full WAN replacement with built-in firewall-as-a-service and broader cloud-native support for complex hybrid environments.
Best For
Teams that want strong ZTA at the application level and are comfortable pairing it with separate DNS or web layers.
Self-hosted VPN and Access Server Options
Some organizations decide that they don’t need a full SASE or Zero Trust security platform. They revert to self-hosted VPN servers in their own cloud environments or on premises networks, then add DNS security on top.
Common self-hosted tools include OpenVPN Access Server, WireGuard-based gateways, and IPsec solutions such as StrongSwan.
OpenVPN Access Server

OpenVPN Access Server is a commercial build of the OpenVPN protocol that you host yourself. It runs in your own data centre or in cloud environments such as AWS or other providers. Administrators control how servers route traffic, which subnets are reachable, and how clients authenticate.
OpenVPN vs. Perimeter 81
Self-hosting gives direct control over IP addresses, routing, and placement. Teams can integrate VPN servers into existing firewalls and network designs, and can choose where to store logs and network metadata.
Where Perimeter 81 Wins
Perimeter 81 and other SASE tools bring ZTA controls, secure web gateway functions, and cloud security policies that go beyond connectivity. Self-hosted VPNs focus on transport and need extra tools for DNS filtering and policy enforcement.
Best For
Organizations with network skills that want to control where gateways live and how they integrate with existing network security.
WireGuard and IPsec gateways

WireGuard and IPsec gateways offer site-to-site and remote access VPNs using established protocols. They are common in setups where on-premises and cloud networks must be linked and where teams are comfortable managing routing and firewall rules.
WireGuard and IPsec gateways vs. Perimeter 81
- WireGuard and IPsec gateways are raw tunneling technologies you host and manage yourself, while Perimeter 81 is a managed, cloud-based platform that bundles networking, security, and access control into a single service.
- With WireGuard/IPsec, you handle your own scaling, redundancy, and configuration across gateways and clients, whereas Perimeter 81 offloads most of that to its control plane, GUI, and hosted infrastructure.
- It gives you very granular, low-level control over tunnels and routing, while Perimeter 81 adds higher-level features like identity-based access, device posture checks, and integrated monitoring on top of the network layer.
Where Perimeter 81 Wins
Perimeter 81 and other SASE platforms wrap connectivity inside a broader Zero Trust architecture, with web security, Zero Trust access, and logging built in. Plain VPN gateways typically need a separate DNS security layer and a separate policy engine.
Best For
They often fit better where an organization already has strong network engineering skills and wants to keep tight control over network paths. For some, these gateways are a modern answer to legacy VPNs that have outlived their support cycles.
Lightweight VPN alternatives for small teams
Smaller organizations, start-ups, and teams that support a limited number of remote workers often find SASE and Zero Trust platforms too large for their needs. Lightweight VPN services are more attractive in these cases, especially when they pair well with DNS filters.
Windscribe (ScribeForce)
Windscribe is widely known as a consumer VPN, but its ScribeForce feature turns it into a team VPN service. Organizations can buy a pool of accounts for their users, manage billing centrally, and provide a simple remote access VPN for remote workers.
Windscribe vs. Perimeter 81
- Windscribe ScribeForce is basically a team layer on top of a consumer VPN focused on secure internet access, while Perimeter 81 is built as a business network security platform with ZTA to internal apps and networks.
- With ScribeForce, your team mainly gets shared VPN accounts, static IPs, and policy-based browsing, whereas Perimeter 81 adds private gateways, site-to-site networking, and fine-grained app-level access control.
- Windscribe’s strengths lie in privacy-oriented VPN features and flexible browsing rules, while Perimeter 81 leans into broader SASE / ZTNA use cases like segmenting company resources, device posture checks, and centralized security policy.
Where Perimeter 81 Wins
Perimeter 81 and other SASE vendors offer network security, Zero Trust architecture, secure web gateway functionality, and broader access management tools that go beyond a VPN.
Best For
Small teams that want a straightforward cloud VPN and plan to add DNS filtering with a service like Control D for stronger content filtering and threat protection.
UTunnel
UTunnel offers business VPN and cloud VPN services where you can deploy dedicated VPN servers in your own cloud accounts or on premises and manage them through a web console.
UTunnel vs. Perimeter 81
- UTunnel gives you dedicated VPN servers in your own cloud or on-prem, and now offers ZTA and mesh networking features on top. It still stops short of a full SASE suite, which is where Perimeter 81 keeps an edge.
- With UTunnel, you mostly manage tunnels, servers, and basic user access yourself, whereas Perimeter 81 adds identity-based policies, per-app access, device posture checks, and central security controls.
- UTunnel is strongest as a simpler business VPN replacement, while Perimeter 81 is better suited for companies that want to replace legacy VPNs with broader ZTA for many apps, locations, and teams.
Where Perimeter 81 Wins
Perimeter 81 and other Zero Trust security platforms offer more comprehensive security policies, secure web gateway options, and ZTNA controls that UTunnel does not attempt to match.
Best For
It suits simple site links, remote access, and cases where a full SASE stack is unnecessary.
FAQ about Perimeter 81 Alternatives
How Much Does Perimeter 81 Cost?
Perimeter 81 uses tiered per-user pricing with minimum seat counts on most plans. Lower tiers target smaller teams that need secure remote access and basic Zero Trust. Higher tiers add stronger security controls and more locations, with enterprise plans for custom needs. Pricing shifts over time, so check Perimeter 81’s site for current numbers.
Is Perimeter 81 a VPN?
Perimeter 81 began as a cloud VPN service, and it still uses VPN tunnels to provide secure remote access between users and networks. Today, it’s better described as a ZTNA and SASE platform. It combines remote-access VPN functionality with Zero Trust architecture concepts, secure web gateway controls, and cloud security features, enabling organizations to control access to company resources through identity-based policies rather than simple network rules.
Is Perimeter 81 Safe?
Yes, it is. Perimeter 81 is a security-focused platform that uses strong encryption, supports multi-factor authentication, and applies Zero Trust policies and network access control. The vendor holds several certifications and markets the service as protection against cyber threats. As with any cloud service, safety still depends on configuration, access control, other security layers, and regular reviews and monitoring.


