Best Cloudflare Alternatives for CDN, DNS, Zero Trust, Tunnel, and Workers
We discuss the best alternatives to Cloudflare, based on factors like price, features, UX, customer support, and user reviews.

Cloudflare sits in many stacks. Teams use it as a Content Delivery Network (CDN), a Domain Name System (DNS) service, a Zero Trust gateway, a VPN-style client, a tunnel, and a serverless platform. That mix explains why, if you’re searching for Cloudflare alternatives, you’ll find very different answers.
This guide walks through the main Cloudflare product areas and shows you where other vendors fit. You’ll see where a new Content Delivery Network provider makes sense, where a dedicated DNS and security layer belongs, and where Workers-style platforms compete. By the end, you’ll have a clear shortlist of the best Cloudflare alternatives for your own stack.
TL;DR: Our quick comparison table has all you need to know:
| Cloudflare Product | Best Alternative | Best Use Case |
|---|---|---|
| DNS & Zero Trust | Control D | Teams needing granular security, 99.98% malware blocking, and Traffic Redirection without CDN bloat |
| Enterprise CDN | Akamai | Large enterprises requiring maximum global reach and heavy DDoS mitigation. |
| Cloud CDN | Amazon CloudFront | Teams already integrated into the AWS ecosystem needing pay-as-you-go scale |
| Developer CDN | Fastly | Developers requiring real-time control and instant cache purging |
| Workers (Edge) | Netlify Edge | Front-end teams deploying serverless logic alongside their web builds |
| Tunnel / VPN | Tailscale | Secure, mesh-based remote access for internal tools without central gateways |
| Privacy VPN | Windscribe | Protecting remote workers on public Wi-Fi with strong blocking features |
Cloudflare at a Glance and How Alternatives Line Up
Before comparing vendors, it helps to see Cloudflare’s main roles side by side. That makes it easier to see which piece you want to replace. It is also worth noting that, while Cloudflare is fast, its history of outages has affected thousands of users and cost millions of dollars in lost revenue. Reliance on a single vendor for all these roles creates a single point of failure, which is why many teams now look to diversify.
Teams use Cloudflare for four broad jobs:
- DNS, Gateway, and Zero Trust: Cloudflare operates public DNS services like 1.1.1.1, secure DNS resolvers for filtering, HTTP filtering through Gateway for threat protection, and Zero Trust for identity-aware access control. These enable remote access to internal web applications and private network resources via policies based on user identity, device posture, and other contexts.
- Cloudflare CDN: Cloudflare's CDN caches static assets on edge servers across its global network, enhancing website performance by serving content closer to users and providing DDoS protection along with web application firewall (WAF) rules.
- WARP and Tunnel: WARP provides a client for mobile devices and desktops that routes web traffic privately through secure tunnels, often using WireGuard or MASQUE protocols for encrypted connectivity. Cloudflare Tunnel complements this by connecting internal services to the global network without public IP addresses, supporting features such as private network access and post-quantum cryptography.
- Cloudflare Workers: Runs JavaScript and other runtimes on edge servers, close to the user, for API logic, image resizing, image processing, video delivery support logic, and other application performance tweaks.
From that view, you can see four groups of Cloudflare alternatives:
- DNS and Zero Trust tools like Control D and Cisco Umbrella focus on DNS service, secure web filtering, website security, and policy-driven access control.
- CDN peers such as Akamai CDN, Amazon CloudFront, Fastly, and Microsoft Azure CDN.
- VPN and tunnel tools like Windscribe for stable remote access from multiple devices.
- Workers-style edge platforms for serverless logic on a global CDN.
In the next sections, we structure our comparison of Cloudflare alternatives around these four key groups.
DNS, Gateway, and Zero Trust Alternatives to Cloudflare
Some teams rely primarily on Cloudflare for DNS and security. In that case, the core questions focus on security features, enhanced security, access control, and data protection for web apps and internal services.
1. Control D (Best Cloudflare DNS Alternative)
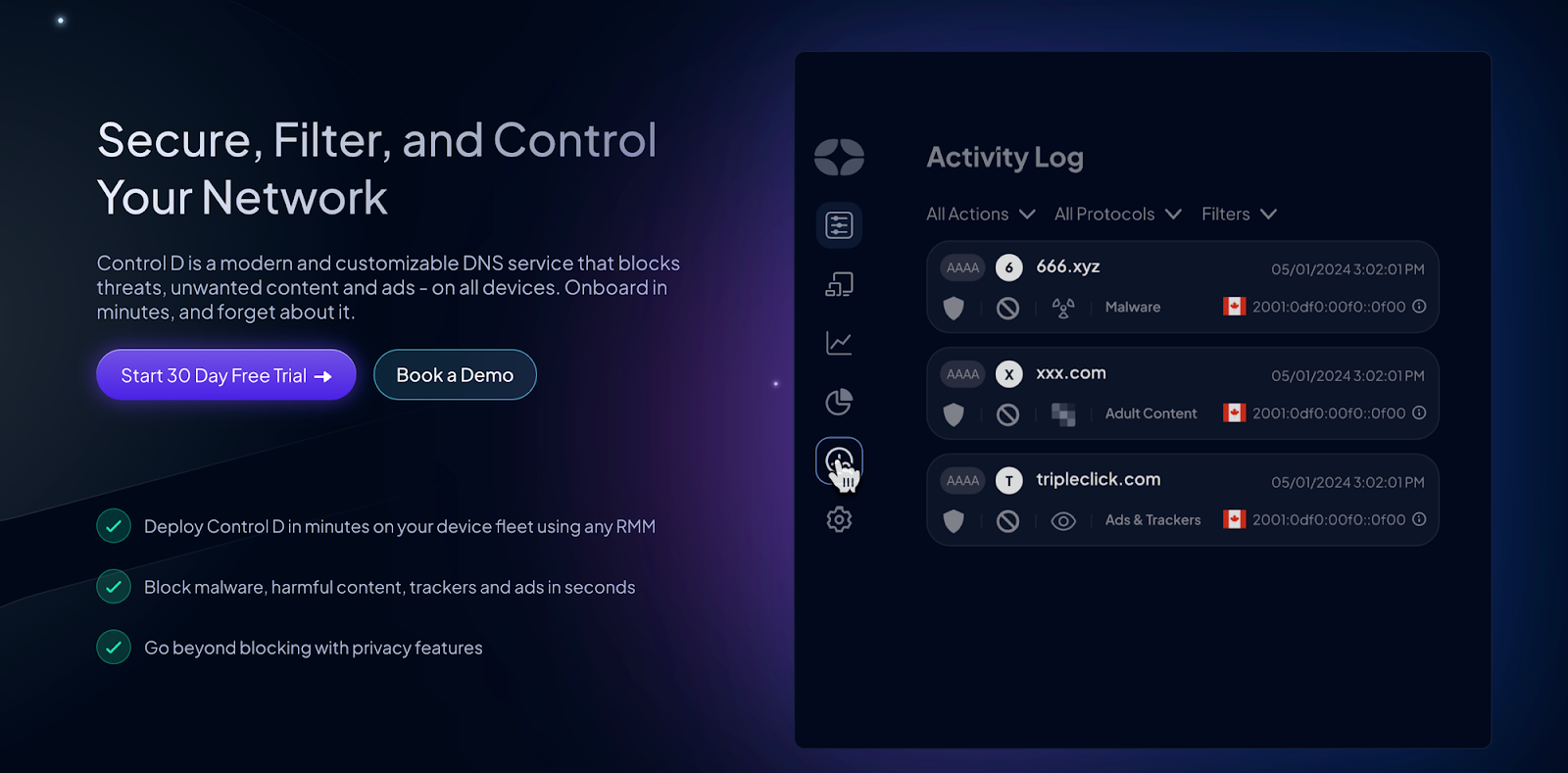
Control D provides advanced malware protection, flexible content blocking, and a large catalog of 1,000+ blockable Services. It supports all modern DNS protocols, SIEM log streaming, ad and tracker blocking, and advanced Geo-Custom Rules that can apply country and ASN conditions to block, redirect, or bypass traffic.
The platform includes Traffic Redirection through over 100+ global proxy locations with rules per domain and per Service, along with a fallback option. Analytics live directly in the dashboard, with per-user reporting, daily, weekly, or monthly scheduled reports, and selectable data storage regions in North America, Europe, or Australia, plus the option of a custom region.
Key Advantages
- Clear focus on comprehensive security at the DNS and HTTP layers, instead of trying to act as a full content delivery network.
- Independent benchmarks show Control D blocks 99.98% of malicious domains, significantly outperforming Cloudflare’s 95.82% block rate.
- More cost-effective scaling for Zero Trust, starting at $2/endpoint/month compared to Cloudflare Gateway’s $7/user/month entry point. Cloudflare often forces you to purchase their entire Zero Trust suite just to access Gateway features, meaning you pay for products you may not use.
- With Control D, every customer gets the full feature set regardless of plan type, including scheduled reports, flexible data storage choices, and SIEM streaming, and future feature updates are included in the price. Some features offered by Cloudflare – such as SIEM log streaming and per-user reporting – are only available on the Contract plan, which can further hike up costs if you require a specific feature not available in the lower plans.
- A strong match for companies that want a separate DNS and gateway, independent of any single CDN provider.

Trade-offs
- No CDN or Workers equivalent, so you still need to pick another CDN service for static assets.
- Admins still need some technical expertise to design effective policies, though the daily work remains manageable.
Customizability
Control D offers granular configuration through Geo-Custom Rules that use country and ASN data, per-domain and per-service redirection, and policies and reporting that can be scoped to individual users or groups. Customers can choose from several analytics storage regions and can request a custom region for an additional fee.

Cloudflare Gateway DNS policies cover domains, content, and security categories, IPs, and geolocation, such as source or resolved country. ASN-based filtering is available through Cloudflare’s complex custom WAF and IP Access rules, but the standard DNS policy builder does not expose controls for the resolved destination’s ASN.
UX and Onboarding
- Control D’s onboarding process eliminates the complex “wall of text” approach often associated with Cloudflare, allowing for setup in minutes without specialist technical skills.
- The dashboard is designed around straightforward management of DNS configurations, with documentation available for those who want extra guidance.
- A recent redesign modernised the interface while keeping navigation quick and direct.

Support
- Users report fast replies to tickets, along with detailed explanations and practical recommendations to reduce the risk of repeat problems.
- The Barry chatbot strengthens support by answering 99% of queries within seconds, solving everything from technical configuration issues to general questions without waiting for a human agent.

Check out our individual comparison posts to go deeper:
2. Cisco Umbrella
Cisco Umbrella, which grew out of the OpenDNS acquisition, offers malware and phishing protection, Geo-IP blocking, and deployment options for both PCs and mobile devices – features almost identical to Cloudflare.
It allows data storage in either North America or Europe and is sold through a range of plan families, including Umbrella DNS Essentials and DNS Advantage, Umbrella SIG Essentials and SIG Advantage, and Secure Access Essentials and Secure Access Advantage.
Key Advantages
- Strong place in large Cisco estates that already use Cisco firewalls or AWS services for parts of the stack.
- Secure web gateway for HTTP inspection and web application control. Integrations with Cisco Secure Client for remote access and private network links.
- Various paid plans and enterprise plans for different seat counts.
Trade-offs
- The Cisco Umbrella Roaming Client reached end of life on April 2, 2025. Organizations still using it are now on unsupported software and face a mandatory migration to the Cisco Secure Client.
- In Cisco’s product strategy, DNS security is only one piece of a larger cybersecurity portfolio, which can make it hard to see where Umbrella ends and other Cisco products begin.
- The large number of overlapping plans increases complexity, and neither Cisco Umbrella nor Cloudflare makes onboarding feel straightforward.
3. WebTitan

WebTitan provides a DNS filtering solution built with Managed Service Providers (MSPs) and mid-size companies in mind. It is particularly effective for offices, schools, and service providers that need to manage web access across distributed networks.
The platform pairs this control with detailed reporting that visualizes web traffic by category, user, and time. On the security side, its cloud-based architecture helps keep the DNS layer available even during large attack spikes against resolvers.
Key Advantages
- Simple commercial model that suits resellers.
- Transparent pricing for quoted user counts.
Trade-offs
- User interface feels older and clunky in places.
- Does not offer Geo-IP blocking/Geo-Custom Rules, a list of blockable Services, or a community support forum – most of which are provided by its competitors.
Cloudflare CDN Alternatives from the Edge Network Market
If your main concern is faster sites and web application delivery, you are looking for Cloudflare CDN peers. These vendors focus on high-performance CDN delivery, DDoS mitigation, WAF rules, and reliable performance for static and dynamic content.
1. Akamai CDN
Akamai sits at the mature end of the market, continuing to carry a massive share of global traffic for large brands that demand enterprise-grade performance. With its exceptionally wide network of server locations that cache content close to users, it fits best for teams that prioritize global reach and reliability, particularly those requiring strong DDoS protection baked directly into the CDN service.
Key Advantages
- Strong DDoS protection and data protection for traffic that needs comprehensive security.
- A wide list of server locations that improve website performance across many regions.
- Suitable for teams with high web traffic and strict website monitoring needs.
Trade-offs
- Pricing often sits in the upper range. Smaller sites may find affordable pricing easier with other vendors.
- Setup expects some technical expertise. Users unfamiliar with enterprise CDNs may prefer a simpler panel.
2. Amazon CloudFront (AWS)
Amazon CloudFront runs directly on the AWS edge network, making it the logical choice for teams already using EC2, S3, or other Amazon services for their origin. For these users, it enables consolidating the entire stack, from storage to delivery, into a single environment with a clear, pay-as-you-go pricing model.
On the technical side, CloudFront goes beyond simple caching by integrating tightly with AWS Shield and WAF for robust DDoS mitigation and security. It also supports modern delivery protocols like HTTP/3 and handles complex dynamic tasks, such as on-the-fly image resizing and video streaming, to ensure high application performance.
Key Advantages
- Pay-as-you-go model with request pricing published in detail, supporting transparent pricing.
- Flat-rate options that bundle CloudFront with AWS WAF, DDoS features, and DNS, useful for comprehensive security around web apps.
- Strong fit when you already use other AWS services as origin.
Trade-offs
- Console and terminology can confuse users unfamiliar with AWS.
- Rules and cache behaviour can feel dense without prior technical expertise.
3. Fastly
Fastly distinguishes itself with a developer-first approach, catering to tech-savvy users who demand granular control. It is the ideal fit for teams that need to fine-tune caching, manipulate headers, and manage complex logic directly at the edge via VCL or modern languages. On the security front, Fastly integrates a Next-Gen WAF and built-in DDoS mitigation, providing advanced protection for APIs and web apps without sacrificing performance.
Key Advantages
- Fine-grained control and feature-rich rules for caching and security.
- Strong data for teams that care about application performance and latency.
Trade-offs
- Fastly is a "developer-first" platform. To unlock its full power, you often need to know VCL. It is not a "click-and-go" solution like Control D.
- Pricing can climb as traffic grows, so many teams compare Fastly with other best Cloudflare CDN alternatives before committing.
4. Microsoft Azure CDN
Microsoft Azure CDN lets teams bring the content delivery layer into their existing cloud environment, making it a perfect fit for those who want to keep compute, storage, and delivery under one roof. It is designed for users who prioritize deep integration, enabling them to manage load balancing and web application security without juggling external vendors.
Uniquely, the service offers multiple "flavors" of delivery, allowing you to back your CDN with nodes from partners like Verizon or Akamai. On the security front, it includes built-in SSL and custom HTTPS support, while seamless hooks into Azure Front Door provide advanced WAF rules and DDoS mitigation to protect your critical assets.
Key Advantages
- Single billing line for CDN and Azure, with paid plans aligned to normal Azure usage.
- Direct integration with logging and website monitoring tools in Azure.
- Good fit for enterprise plans that already include security products.
Trade-offs
- Panel and terms feel Azure-centric, which can slow down users unfamiliar with the platform.
- Some regions might not match the reach of Cloudflare’s global network.
5. Bunny.net (value-focused CDN)
Bunny.net frequently tops the list for small to mid-size sites that want enterprise-grade speed without the opaque pricing models of larger competitors. It fits best for teams that value transparency and simplicity, offering a hassle-free control panel and a clear rate card that keeps costs predictable.
On the technical side, it backs this affordability with a capable global network and built-in image processing features that reduce payload sizes on the fly. While it focuses on ease of use, it also includes essential website monitoring and basic security features, making it a reliable choice for projects that need speed and safety without the bloat.
Key Advantages
- Simple, hassle-free sign-up and simple setup process that works in just a few clicks.
- Clear per-GB prices and region lists, which appeal to teams that want tight cost control.
Trade-offs
- Fewer advanced features than Cloudflare or Fastly. Some plans have limited features compared with enterprise CDNs.
- Some larger companies still prefer Cloudflare’s enterprise plans or Akamai for very high traffic.
Best Cloudflare Workers Alternatives
Cloudflare Workers runs code on edge servers in Cloudflare’s global network. That helps with low-latency web apps, API routing, load balancing logic, image processing, image resizing, and small bits of application performance tuning.
Some teams want similar tools from other providers. The aim in this section is not to replace Cloudflare’s CDN, but to match the idea of serverless logic near users.
1. Netlify Edge Functions

Netlify Edge Functions are ideal for front-end teams adding serverless logic within the Netlify ecosystem. They integrate seamlessly into existing workflows, custom domains, and deploy pipelines. Powered by the Deno runtime and standard Web APIs, they eliminate complex build configurations. By running on Netlify’s global CDN, these functions execute near the user, delivering low-latency routing and fast API performance.
Key Advantages
- Helps front-end teams adjust responses without touching origin code.
- Works close to where static assets live, so many responses feel like quick access even under load.
Trade-offs
- Netlify Edge Functions use Deno, not Node.js. While Deno is modern and secure, it means you cannot simply drop in your existing npm packages without checking for compatibility or using polyfills.
- While generally faster than full serverless containers, they can still experience slight "cold start" latency compared to Cloudflare’s near-instant isolate model, especially on less popular routes.
3. AWS Lambda@Edge
Lambda@Edge is the natural extension for teams who need to push serverless logic out to CloudFront’s global edge locations. It serves as a powerful layer for modifying requests and responses in flight, giving developers precise control over headers and routing without hitting the origin.
On the security and integration front, it unifies your stack by combining with AWS Shield and WAF for robust DDoS mitigation. Furthermore, because it lives within the AWS environment, it provides low-latency hooks into other essential services, easily connecting edge logic to centralized data stores, queues, and storage buckets.
Key Advantages
- Unlike Cloudflare Workers, which requires a separate billing and auth environment, Lambda@Edge lives inside your existing AWS account.
- You can manage access via standard IAM roles and consolidate billing with your EC2 and S3 usage.
- You can securely trigger DynamoDB for global, low-latency data access, write logs directly to CloudWatch, or drop files into Kinesis Firehose without managing API keys or external connections.
Trade-offs
- Lambda@Edge is significantly more expensive than standard Lambda functions and often costs more than Cloudflare Workers for high-volume, simple tasks.
- Logs are stored in CloudWatch in the specific region where the code executed (not just one central place), which can make troubleshooting global issues tedious.
- Lambda@Edge can experience latency penalties when spinning up new instances after periods of inactivity.
Note: In all these cases, Control D can sit beside the platform as a DNS and gateway layer. It doesn’t run code; it guards the path to those services.
Alternatives for WARP, Tunnel, and Secure Remote Access
Cloudflare WARP and Cloudflare Tunnel sit closer to VPN and mesh networking tools. They route traffic from users to a private network or to Cloudflare edge points and then back to the origin. That model helps with remote access to internal web apps and small services.
Several tools cover a similar need.
1. Tailscale

Tailscale builds a mesh VPN on top of the modern WireGuard protocol, allowing devices to form a private network where connections are direct and encrypted. With lightweight clients for both desktops and mobile devices, it ensures seamless remote access across your entire team without the bottleneck of a central gateway.
The platform differentiates itself by attaching identity to every node, moving beyond simple IP-based trust. This allows administrators to define precise access control rules in the central console, ensuring that only explicitly authorized users and devices can access the services.
Key Advantages
- Quick rollout for multiple devices with a light agent.
- Flat network diagrams that feel natural for developers who work with small services.
Trade-offs
- The "always-on" mesh connection can drain batteries significantly faster on iOS and Android devices than standard VPNs.
- You have to rely on Tailscale’s central coordination server and a third-party Identity Provider (like Google or Microsoft) to access your own network.
- Because it runs in "userspace" rather than kernel mode, it is generally slower than a raw WireGuard installation for high-bandwidth transfers.
2. Ngrok

Ngrok started as a favorite for local development but now serves a broader role in connecting private apps to the public web. It is best suited for developers who need to instantly expose local servers or private services via public URLs for testing, demos, or webhooks.
On the technical side, it adds a layer of security and visibility over these tunnels. It handles TLS termination and SSL management automatically, while offering deep inspection tools to analyze HTTP traffic and real-time monitoring options to keep track of tunnel performance.
Key Advantages
- Very fast setup for testing and demos.
- Works well for small internal tools that need quick access from outside the office.
Trade-offs
- On the free plan, public URLs change every time you restart the tunnel, breaking webhooks and requiring constant reconfiguration.
- Strict rate limits on connections and bandwidth can block access during load testing or heavy API usage.
- While great for dev, pricing scales steeply for production use (custom domains, SSO, static IPs) compared to dedicated edge platforms.
3. Windscribe
Windscribe bridges the gap between simple consumer VPNs and advanced privacy tools, making it a strong choice for both beginners and power users. It is well-suited for those who want a generous free tier (10GB/month) or teams that need domain-level blocking integrated directly into their VPN client.
Beyond standard encryption, Windscribe offers R.O.B.E.R.T, a unique server-side tool that blocks ads, trackers, and malware at the DNS level before they reach your device. It also provides powerful browser extensions that can spoof your GPS, timezone, and user agent to prevent fingerprinting, along with options for static IPs (datacenter or residential) for users who need consistent access to restricted networks.
Key Advantages
- Windscribe pairs perfectly with Control D. The former handles the encrypted tunnel, while Control D acts as the customizable DNS layer.
- The browser extension is robust enough to use as a standalone "lite" VPN for quick browsing sessions without tunneling the whole device.
Trade-offs
- The free tier limits bandwidth to 10GB/month and restricts access to certain premium server locations.
4. Mullvad
Mullvad is the "purist's choice" for privacy, designed to require zero personal information. It replaces standard subscriptions with a flat monthly rate and an anonymous account system where you log in with a random 16-digit number—no email needed. Built on the WireGuard protocol for high-speed stability, Mullvad simplifies "multi-hop" configurations, routing traffic through servers in separate jurisdictions to maximize anonymity.
Key Advantages
- You can pay via cash or crypto and sign up without an email, creating a genuine barrier between your identity and the service.
- The price has remained €5 per month for over a decade, avoiding the renewal price hike tactics common in the industry.
Trade-offs
- Mullvad does not optimize servers for unlocking streaming platforms; if it works, it's luck, not a feature.
- There is no free version or free trial (other than a money-back guarantee); you must pay to use the service.
- The client is utilitarian and simple, lacking some of the "quality of life" dashboard widgets found in more consumer-focused apps.
Read More: How to Secure Remote Workers: Tools & Best Practices
How to Pick the Right Cloudflare Alternative Stack
Cloudflare covers a wide surface. Replacing it often means swapping in several tools and keeping the pieces aligned. A short, practical path helps.
Step 1: Decide which Cloudflare role you care about most
Start by listing where Cloudflare sits today:
- As Cloudflare CDN in front of your site.
- As a DNS and gateway for web application security and website security.
- As a WARP or Tunnel for remote access to internal tools.
- As Workers runtime for edge logic.
That list shows which part you need to move first.
Step 2: Pick a CDN provider for public sites
For public sites, choose a CDN provider based on origin, traffic level, and team skill:
- Heavy use of AWS: Favour Amazon CloudFront, pair it with AWS Shield, AWS WAF, and other AWS services for comprehensive security. You get pay-as-you-go billing and clear links to other AWS services.
- Heavy use of Azure: Look at Microsoft Azure CDN and Azure Front Door. This keeps web application firewall, DDoS protection, and website performance tuning in one cloud.
- Need strong DDoS protection and enterprise-grade performance: Shortlist Akamai CDN, CloudFront, and Fastly as the best Cloudflare CDN alternatives for very high web traffic.
- Tight budget or small projects: Look at Bunny.net for affordable pricing, transparent pricing, and a clear focus on reliable performance.
At this stage, check for free-tier or free-plan options. Cloudflare offers a Free Plan with basic CDN and DDoS protection. Some alternatives also offer trials or free developer plans.
Step 3: Add a DNS and security layer
Next, decide how you’ll handle DNS service, web application security, and comprehensive security for users and devices. A practical way to think about it:
- If you want a DNS and HTTP gateway that is independent of any content delivery network, add a tool like Control D in front of users. That gives you enhanced security and security features that follow users on and off the office network.
- If your company already uses Cisco everywhere, Cisco Umbrella may feel more natural.
- If you work as an MSP, WebTitan or similar multi-tenant tools give you core features that suit multi-client work.
Step 4: Map your remote access story
If WARP or Tunnel plays a big part in your stack, plan a new route for remote access. Ask a few questions:
- Do teams need a mesh private network where every device can reach every service.
- Do they just need tunnels for demos and short-lived web apps.
- Do they need a full consumer-style VPN for privacy.
Mesh tools like Tailscale cover always-on remote access to internal services. Tunnel tools like Ngrok handle demos and temporary web apps. Privacy VPNs like Windscribe serve users who mainly need encrypted web traffic from shared networks.
Step 5: Plan for Workers-style logic
If you rely heavily on Workers, you need a new home for edge logic.
- Staying in the same cloud as your main hosting, for example, Lambda@Edge in AWS, which you pair with CloudFront and AWS services.
- Moving to Netlify Edge Functions when your front-end team already deploys there.
Key points to compare:
- Latency from users to edge servers.
- Limits around memory, runtime, and edge storage.
- How easy it feels to connect these functions with DNS, CDN, and application code.
Again, Control D plays the same role as before. It guards DNS and HTTP traffic, then hands requests on to your content delivery network and Workers-style platform.
Step 6: Look at Pricing
Pricing across Cloudflare alternatives often looks neat on the surface and complicated in practice. A short checklist helps. Look at:
- Where paid plans start for production use. Cloudflare Pro costs around $20 to $25 per month, while Business and enterprise plans climb from there.
- Which features hide behind higher tiers. For example, Cloudflare often restricts essential features like SIEM log streaming and per-user reporting to their Enterprise "Contract" plan, which can significantly hike up costs if you need compliance-level data.
- Whether pricing follows a pay-as-you-go model, a flat monthly tier, or a mix.
- Whether DDoS handling and WAF use extra add-ons.
- How each vendor treats technical support at lower tiers.
- Some vendors highlight phrases like affordable pricing and hassle-free setup. Take that as a prompt to test the real simple setup process yourself, not as a guarantee.
FAQs about Cloudflare Alternatives
Is There Anything Better than Cloudflare?
It depends on your specific goals. For CDN performance, competitors like Akamai, CloudFront, Fastly, and Bunny.net often outperform Cloudflare in specific regions on latency or price. For DNS, alternatives like Control D, Quad9, and NextDNS offer superior privacy controls and filtering. The “best” choice requires mapping your specific budget, jurisdiction, and feature needs to your risk profile and validating it with real-user testing.
Does the FBI Use Cloudflare?
Public records confirm the US government relies on Cloudflare, though specific agency lists remain private. Notably, CISA awarded Cloudflare a contract to manage authoritative DNS for the .gov top-level domain, covering numerous federal and law enforcement sites. Additionally, Cloudflare’s transparency reports detail how they handle law enforcement data requests. While this evidence confirms infrastructure usage and cooperation, the specific details of internal FBI networks remain undocumented in open sources.
Is There a Better DNS than Cloudflare?
Cloudflare’s 1.1.1.1 is fast but rigid. Quad9 prioritizes security, while NextDNS offers granular profiles. That said, Control D is a strong upgrade candidate. In one independent DNS test, it matched top-tier speeds and reached a 99.97% malware block rate, compared with 3.93% for Cloudflare, while still offering unique traffic redirection tools. By combining advanced filtering with proxy features, Control D offers a powerful, customizable security layer that adapts to your specific threat model.


