The 30 Biggest Data Breaches of the Last 20 Years
Learn about the 30 biggest data breaches since 2005, ranked by users or records, with data types, causes, and sources.

There’s a good chance your sensitive personal information has already been exposed in a massive data breach. With billions of records compromised every year, the question is no longer if your data is out there, but how many times.
That’s why we’ve created this guide ranking the biggest data breaches by the number of affected users. We explain what happened in each case, what data types were compromised, and how attackers gained access. We also outline direct, actionable steps you can take to improve your data security.
How We Ranked the Largest Data Breaches by Affected Users
The numbers in the most significant data breaches can be dizzying. Billions of records, millions of people. But what really counts as the “biggest”? Some lists rank by the sheer number of records, which can be misleading. One person might have 10 records in a single database, after all.
We rank the biggest data breaches first and foremost by the number of people affected. Human impact is what matters. If a confirmed user count is unavailable, we use record counts and label them clearly. We also label “exposure” where databases were left open and “improper collection/scraping” where data was gathered via public interfaces or app permissions.
A Look at Common Attack Methods and the 30 Biggest Incidents
Trends in Data Breaches Since 2010
Looking back at the total data breaches over the last decade or so, a few patterns emerge. Security researchers have pointed out that the ways attackers gain access have shifted. And the most common attack methods often fall into three main categories: Targeting people, exploiting technical flaws, and taking advantage of simple mistakes.
Earlier breaches frequently focused on exploiting software flaws directly. Now, many attacks start with the human element. Phishing for stolen credentials is a primary entry point. From there, attackers look for misconfigured cloud infrastructure or poorly secured internal systems.
The type of customer data being targeted has also changed. While email addresses and passwords are still valuable, attackers are increasingly after high-value personal data that can be used for immediate financial fraud. This includes financial data like bank account and credit card details and full sets of personally identifiable information kits.
The 30 Biggest Data Breaches
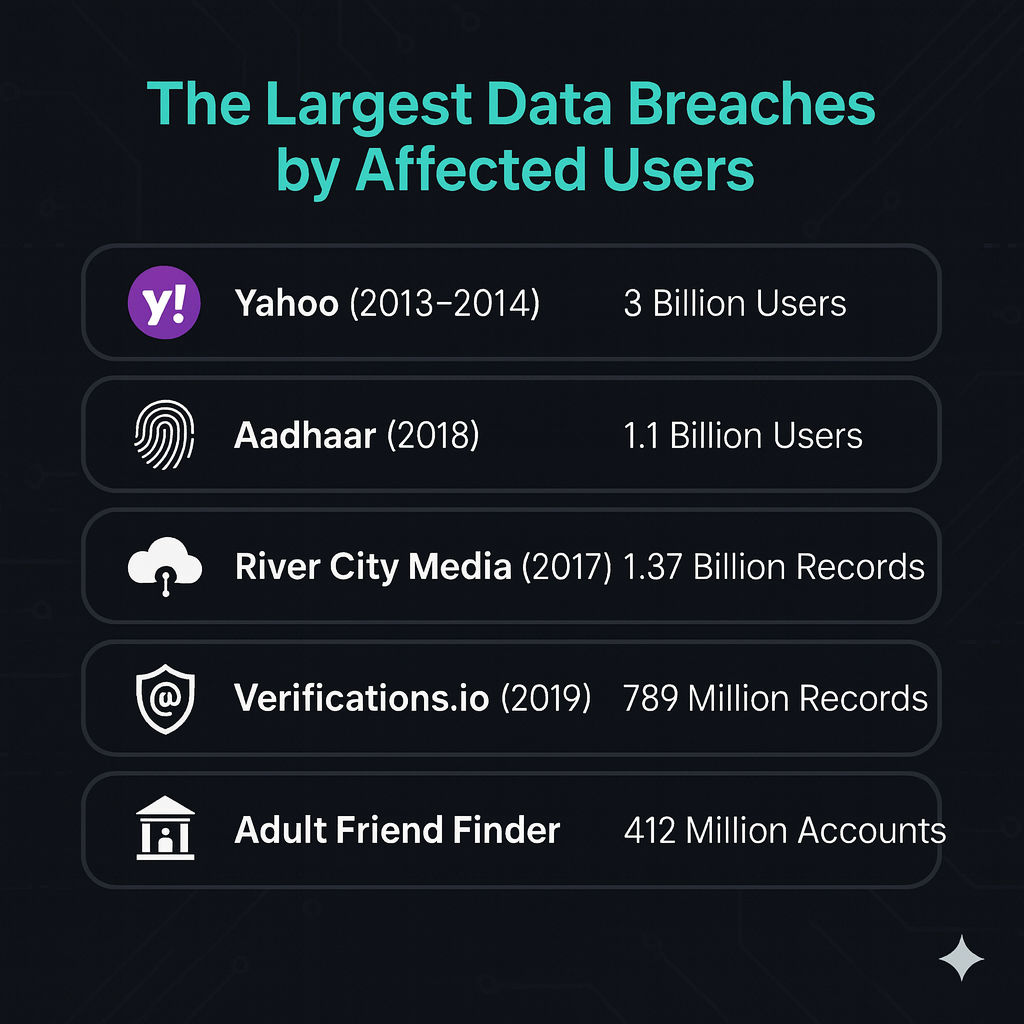
1. Yahoo (2013–2014) – 3 billion accounts (2013) + ~500 million accounts (2014)
In two separate attacks, Yahoo suffered the biggest data breach in history. The 2013 incident ultimately covered all 3 billion accounts; a separate 2014 breach affected about 500 million accounts. The stolen personal data included names, email addresses, phone numbers, dates of birth, and hashed passwords (with some security questions and answers in scope depending on the incident).
2. Aadhaar (2018) – 1.1 billion users; actual scale disputed
India’s national ID ecosystem saw multiple major exposures involving Aadhaar-linked services. Reports described unauthorized Aadhaar lookups via weak or unauthenticated APIs at external providers; claims that all 1.1 billion citizens’ data were exposed are disputed. Exposed data varied by incident and included personal details and, in some cases, bank details.
3. River City Media (2017) – 1.37 billion exposed records
This was not a hack but an accidental exposure of customer records by a massive spamming operation. An unprotected backAn unprotected backup on their cloud infrastructure exposed a huge number of email addresses and user locations, including both IP and physical addresses.
4. Marriott International (Starwood) (2014-2018) – ~383 million guest records
This long-running intrusion began at Starwood hotels and persisted for four years. Marriott revised the initial 500 million estimate to about 383 million guest records. The exposed customer data included names, mailing addresses, passport numbers (including 5.25 million unencrypted and 8.6 million encrypted), and some payment data.
5. Adult Friend Finder (2016) – 412 million accounts
The adult social network suffered a breach that exposed emails and passwords across FriendFinder Networks properties, including some accounts previously marked as deleted.
6. EBay (2014) – 145 million users
One of the earliest significant data breaches at a major tech company, this security incident forced a site-wide password reset. Attackers used employee stolen credentials to access internal systems, exposing names, email addresses, and encrypted passwords.
7. Equifax (2017) – 147 million users
This breach at the credit bureau exposed the core sensitive data needed for identity theft. With Social Security numbers, birth dates, and addresses stolen, millions of people were instantly at risk of criminals opening fraudulent loans or credit cards in their names, damaging their credit reports for years to come.
8. LinkedIn (2012) – 117 million email-and-password pairs (from the 2012 breach, sold in 2016)
The full impact of this breach was felt years later when the stolen data, i.e. 117 million email and password pairs from the 2012 breach, appeared for sale on a dark web market and other hacking-related sites. The initial breach only reported 6.5 million hashed passwords.
9. MySpace (2013) – 360 million accounts
An old social media giant fell victim to a breach later sold on the dark web. The compromised data included email addresses and weakly hashed passwords from legacy accounts.
10. NetEase (2015) – 235 million accounts; disputed
The Chinese email and gaming provider experienced a breach that exposed a huge number of user credentials in plaintext. The data leak included millions of email addresses and passwords, making secondary attacks easy. NetEase however denied a breach.
11. Canva (2019) – 137 million users
The popular design tool was hit by an attack that scraped a large amount of user data. The stolen data included usernames, email addresses, names, user locations, and passwords hashed with bcrypt for non-social logins.
12. Dubsmash (2018) – 162 million accounts
This video-sharing app was one of 16 companies breached by the same group of hackers. The stolen data, which included email addresses and passwords, was later sold on a dark web forum.
13. MyFitnessPal (2018) – 150 million users
The fitness app owned by Under Armour suffered a major data breach affecting its health-conscious user base. The unauthorized access exposed data, including usernames, email addresses, and hashed passwords, which was later sold on the dark web.
14. Capital One (2019) – 106 million customer records
A former cloud employee exploited a misconfigured Capital One firewall in its AWS environment. Exposed financial data for 100 million people in the US and about 6 million in Canada included names, addresses, and credit scores. A smaller set of these records also included SSNs and bank account numbers.
15. Target Stores (2013) – 40 million payment cards + 70 million contact records
This retail breach targeted point-of-sale systems during the holiday season. Attackers stole 40 million payment cards and 70 million records of personal information (names, phone numbers, and addresses), after initial access via a third-party vendor.
16. Heartland Payment Systems (2008) – 134 million credit cards
A landmark case of data theft at a payment processor that affected numerous major credit card companies. Malware installed on their network security systems stole payment data in transit.
17. TJX Companies (TJ Maxx, Marshalls) (2005-2006) – 94 million records
This early, long-running case of data theft demonstrated the vulnerability of retail networks. The attack exposed credit card data and driver's license numbers. While initial reports were around 45 million, later court documents suggested the number was over 94 million records.
18. JP Morgan Chase (2014) – 83 million accounts
The largest breach of a financial institution in history compromised the contact information of 76 million households and 7 million small businesses, including email addresses and physical addresses.
19. U.S. Office of Personnel Management (OPM) (2015) – 22.1 million users
This damaging security incident against the US government exposed the personal data of US federal employees and applicants. The leaked data included background-check information, Social Security numbers, and about 5.6 million fingerprint records.
20. Anthem (2015) – 78.8 million records
One of the largest data breaches in the healthcare sector. This attack on a major US health insurer exposed a vast amount of sensitive data, including protected health information, medical records, names, dates of birth, and Social Security numbers.
21. Home Depot (2014) – 56 million payment cards + 53 million email addresses
Similar to the Target breach, this attack used stolen credentials from a third-party vendor to access Home Depot's network and install malware on their point-of-sale systems, leading to a massive theft of payment data.
22. Sony PlayStation Network (2011) – 77 million accounts
This severe security incident forced Sony to shut down the entire PlayStation Network for 23 days. The breach exposed names, billing addresses, and passwords, and it was suggested that credit card data may have been taken.
23. Uber (2016) – 57 million users
This breach became a case study in how not to handle a data leak after the company paid attackers and concealed the incident. Note that Uber’s former CSO was later convicted for concealing the breach. The exposed data included names, email addresses, and 600,000 US driver licence numbers.
24. National Public Data (2024) – 272 million users
One of the more recent data breaches at a data broker shows the risks of companies involved in selling personal data. Data from 292 million individuals was exposed including the Social Security Numbers (SSNs) for 272 million people, along with names, residential addresses, phone numbers, and birth dates.
25. Verifications.io (2019) – 809 million records
An email validation firm exposed a large database used for list verification. The records included email addresses with personal details and IP addresses. Estimates include about 763 million unique emails.
26. Facebook (via Cambridge Analytica) (2014) – 87 million users
While not a direct hack, this incident involved the improper harvesting of customer data by a third-party app. It amounted to exposing customer data on a massive scale by abusing the application programming interface.
27. Deezer (2019 data, disclosed 2022) – 229 million users
The music streaming service was breached when a third-party partner experienced a security incident. This led to the exposure of user information, including emails, names, usernames, gender, dates of birth, IP addresses, and locations.
28. Shanghai Police Database Leak (2022) – ~1 billion records
This was not a hack but an accidental exposure of a huge police database. The data leak exposed a wide range of sensitive personal data, including names, home addresses, and police case files from an unprotected database.
29. Zappos (2012) – 24 million accounts
The online shoe retailer, owned by Amazon, suffered a breach that compromised the accounts of millions of its customers. Attackers gained direct access to a server, exposing names, email addresses, and postal addresses.
30. Last.fm (2012) – 43 million accounts
The music social network was breached, and the full extent was only realized years later when the leaked data appeared for sale on the dark web. The stolen data included usernames, email addresses, and weakly encrypted passwords.
How to Check Your Exposure and Reduce Your Risk
Even with your best efforts, your data can still appear in a leak. When threat actors combine the personal data stolen through data breaches, the risk multiplies and can lead to account takeover, identity theft, or financial fraud.
So, what can you do about all this? You can’t control a company’s internal data security measures or stop them from getting breached, but you can take steps to protect your personal data.

Check if You’re in a Data Breach
A great first step is to use a service. You can enter your email address, and it will tell you which known data breaches your information has appeared in. It’s a real eye-opener.
If you find out your information was exposed, here is a short checklist to follow immediately to protect yourself:
- Act Quickly: Review your financial accounts, credit card statements, and credit reports for any strange activity or accounts you don’t recognize. Report anything suspicious immediately.
- Freeze Your Credit: Contact the major credit bureaus (Equifax, Experian, TransUnion) and place a freeze on your credit. This stops criminals from opening new financial accounts in your name.
- Get Help: Use resources like the Identity Theft Resource Center. They provide free help and step-by-step plans for victims. You can also look into identity theft protection services, which monitor your information and can help with recovery.
Practical Ways to Reduce Data Exposure
Limit the Personal Data You Share
The less data you make available, the less data can be exposed in a breach. Practise data minimization. When signing up for a new service, only provide the required information. If a field for your phone number or full birth date is optional, leave it blank. For newsletters or services you don’t fully trust, consider using a separate “burner” email address to protect your primary account.
Use Password Protection and MFA
Your first line of defense is good password habits. Don't reuse passwords and use a password manager. It creates and stores a strong, different password for every single account.
Turn on multi-factor authentication (MFA). This is a must-have. Even if someone steals your password, they can't get into your account without a second code, usually from your phone.
Use Unique Email Addresses for Key Services
Your primary email address is often the key to your entire digital life. If that address is exposed in one breach, attackers will try to use it with the stolen password on other sites, like your banking or social media accounts.
You can prevent this by using different email addresses for different purposes. Consider using an email aliasing service (like iCloud’s Hide My Email) that creates a unique, random address for every login. This makes it much harder for data from one breach to affect your other accounts.
Close Accounts You No Longer Use
Every online account you create is a potential liability. Old, forgotten accounts on shopping sites, forums, or social media platforms still contain your personal information. If that service is breached years from now, your data will be exposed. Periodically review your password manager and take a few minutes to permanently delete accounts for services you no longer use.
Add DNS-Layer Security to Block Common Breach Paths
Your network security at home is another layer of defence. DNS sits at the very beginning of almost every connection you make online. When you type a website address, DNS is the first thing that gets you there. This makes it an effective control point for security.
A DNS filtering service like Control D actively blocks malicious and unwanted domains before your device ever connects to them. These types of consumer solutions instantly stops threats like phishing scams, malware, intrusive ads, and trackers, effectively cutting off common paths for credential theft and protecting your privacy.
FAQs About the Biggest Data Breaches
What was the biggest data breach in history?
By account count, the Yahoo breach still holds the record, with roughly 3 billion user accounts affected in 2013, plus a separate ~500 million in 2014.
How did 16 billion passwords get leaked?
This number refers to large compiled credential sets built over years from many breaches and infostealer malware, not one incident. It is a rolling total from multiple sources and changes over time.
What is the largest data breach fine in history?
As of late 2023, Meta (formerly Facebook) holds the record for the largest fine, at €1.2 billion, imposed by European regulators.
Where do most cyber incidents begin?
A large share of the biggest data breaches start with a human element, often phishing for credentials, with many cases then leveraging misconfiguration or weak access controls.

