Best Cybersecurity Tools for Small and Medium Businesses
Protect your business data without the enterprise price tag. We review the top tools for 2026, from Control D to CrowdStrike.

Modern security threats impact businesses of all sizes. The same phishing attempts, ransomware attacks, and account takeovers that hit big firms now hit small businesses and even one-employee consultancies.
Small and mid-market business owners often face a difficult reality: limited resources, strict budgets, and they rarely have a dedicated support team to manage IT operations. This makes cost-effective choices vital. So the question is simple. How do you get practical protection without turning your week into ticket triage?
In this guide, you will see which cybersecurity tools matter most for small and medium businesses. You will learn how these tools fit together as a security program and get a clear view of where DNS filtering with Control D adds an extra layer for every device and every office.
This gives you a clear path to improve cybersecurity for small teams that rely on connected devices, cloud apps, and remote work.
How to Think About Your Security Stack
Many businesses try to buy maximum security without understanding the specific role of each tool. A better approach for small and medium-sized business setups is to pick one or two tools in each layer that you can run well and that match your security needs.
Here is how the main categories break down, including the pros and cons of each as a cybersecurity tool. You will see how these categories support each other, so your cybersecurity efforts feel joined up instead of scattered.
Identity and Access Controls
Before you add other tools, you need basic identity controls. Turn on multi-factor authentication (MFA) for email, admin panels, and remote access. Use a password manager so employees can store unique passwords safely and share access where needed.
Many services now include dark web monitoring, which alerts you if you or your staff’s credentials appear in known leaks. These changes give you strong protection against data breaches that often begin with stolen passwords.
DNS-Based Tools: The First Layer of Cyber Defense
DNS filtering sits between your users’ connection requests and the internet. It stops threats before malware or phishing sites can even load and gives you full visibility into which domains users connect to from office networks and remote work setups.
- Pros:
- Blocks cyber threats at the source before they reach operating systems.
- Very simple setup for office networks and remote workers.
- Provides full visibility into internet usage across connected devices.
- Cons:
- Does not scan files inside a USB drive or local email attachments (needs antivirus software for that).
- Basic versions may lack granular reporting.
Read More: Why Every Business Should Care About DNS Security
Endpoint Detection and Response (EDR)
Endpoint protection has evolved beyond traditional antivirus software. Detection and response tools monitor unusual behaviour on laptops and servers to stop advanced threats.
- Pros:
- Catches ransomware attacks that bypass other filters.
- Can isolate infected machines to protect the rest of the business data and digital assets.
- Often includes threat intelligence and threat detection tools to spot new attack patterns with machine learning and other AI-powered analysis.
- Cons:
- Can be expensive per device.
- Sometimes generates false alarms that need human review.
Read More: How to Prevent Ransomware Attacks: 12 Proven Methods
Next-Generation Firewalls (NGFW)
A firewall monitors traffic entering and leaving your main office network. Modern versions inspect traffic deeply to spot hidden risks.
- Pros:
- Central control for all office networks.
- Can inspect encrypted traffic to find hidden malware.
- Enforces security policies for everyone in the building.
- Cons:
- Does not protect roaming users or mobile devices when they leave the office.
- Hardware costs can be high for small and medium businesses seeking enterprise security features.
Read more: The Problem with Relying on Firewalls for DNS Filtering (And How to Fix It)
Business VPNs
A VPN creates an encrypted tunnel for your data. It is vital for remote access when staff use public Wi-Fi.
- Pros:
- Encrypts traffic, protecting login credentials on public Wi-Fi.
- Allows secure access to internal files for remote work.
- Conceals your IP address from snoops and cybercriminals.
- Cons:
- Can slow down connection speeds.
- Does not filter the content inside the tunnel unless paired with DNS security.
Read More: How to Secure Remote Workers: Tools & Best Practices
Vulnerability and Threat Management
Attackers scan for weak points in software. Vulnerability scanning tools check your systems to find these gaps before hackers do.
- Pros:
- Identifies outdated software and potential security risks.
- Gives a prioritized list of fixes.
- Helps meet compliance rules for sensitive information and supports penetration testing work.
- Cons:
- Only finds problems; does not usually fix them automatically.
- Risks obscuring genuine threats with irrelevant data if not properly configured.
Email and Collaboration Security
Email and chat often carry the first sign of trouble. Fake invoices, login prompts, and file links reach employees every day. Email and collaboration security tools sit in front of those messages and cut down the number of dangerous clicks that reach your staff.
Pros:
- Reduce phishing emails and obvious scams that reach inboxes.
- Scan links and attachments for cyber threats before staff open them.
- Integrate with services such as Microsoft 365 or Google Workspace, so you manage security close to mail and files.
Cons:
- No filter blocks every attack, so you still need employee training and clear rules for handling sensitive data.
- Extra scanning can add small delays to mail delivery for some messages.
- Costs often scale per mailbox, which can add pressure for a small team with tight budgets.
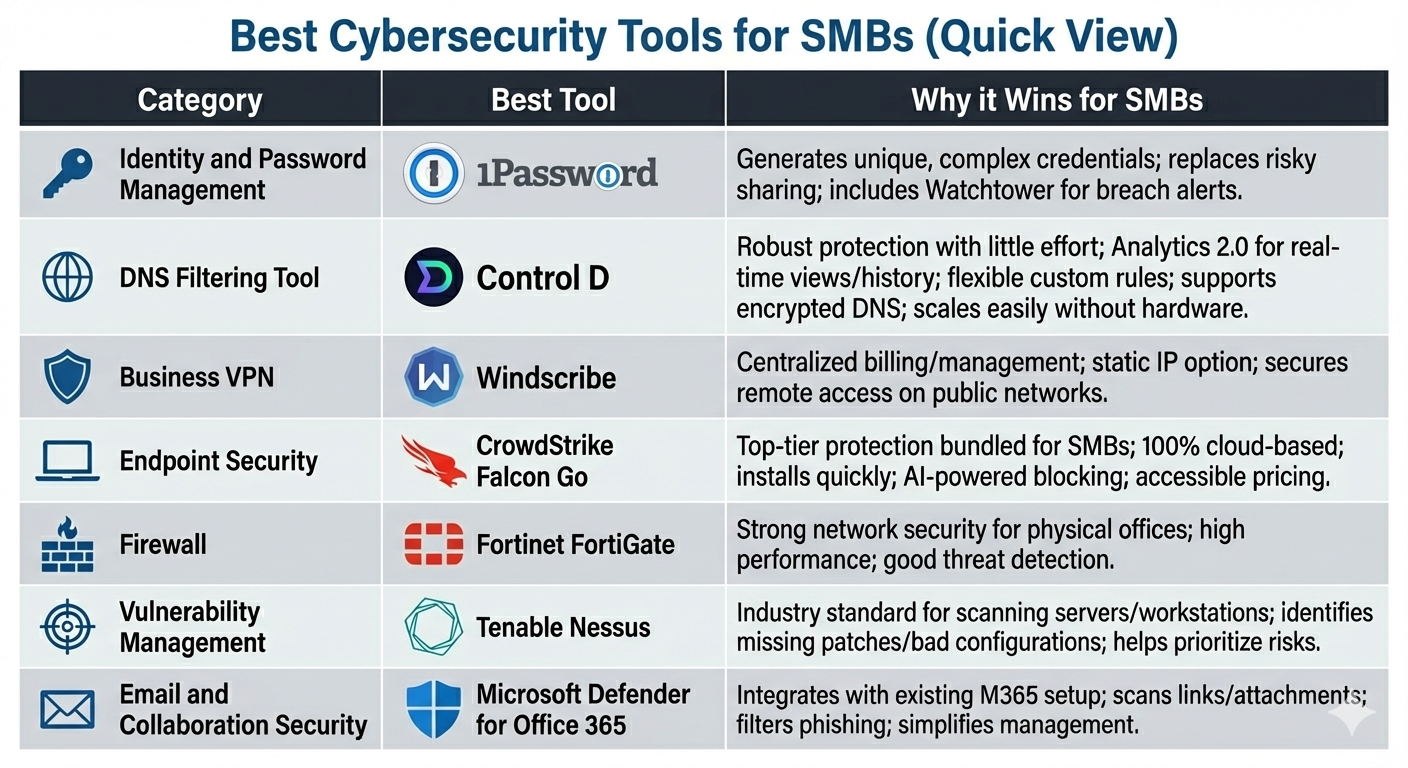
The Best Cybersecurity Tool for Each Category
Now that you understand the layers, here are the specific tools that offer the best value and protection for small and medium businesses. Think of these as starting points rather than the only options for small business security.
DNS Filtering Tool: Control D
DNS filtering is a space where small and medium-sized firms can get robust protection with little effort. Control D is built for that.
You simply point your router or protected devices at Control D. From that point, when users connect to websites or services, Control D checks the requested domain. It blocks domains linked to malware, phishing, and other hostile activity and can help stop threats that try to call home after infection.
Control D stands out as the best bang for your buck for cybersecurity software for small businesses because of its Analytics 2.0 upgrade and flexible security tools. While many services just block silently, Control D gives you critical insights and advanced features that small and medium businesses can actually use day to day:
- Real-time views of DNS traffic so you see what happens on your networks as it happens.
- Roughly one month of history, so you can review incidents and spot patterns instead of losing data after a few days.
- Custom blocklists so you can create your own rules to improve workplace productivity or block specific threats.
- Granular control so you can apply different rules for the marketing team versus the finance team or for office networks versus remote workers.
- Geographic and provider views that show which countries and networks your devices talk to, which helps you spot unusual external threats.
- DNS over HTTPS (DoH), DNS over TLS (DoT), and DoQ support for secure, private queries that prevent ISP snooping and DNS spoofing attacks.
Control D also supports encrypted DNS, so DNS queries travel in a private channel between protected devices and Control D’s servers. That protects sensitive information about which sites employees visit on shared Wi-Fi and other shared links.

It offers affordable protection that easily scales from one employee to a medium business group without needing hardware. For many businesses, Control D becomes the network layer that ties together endpoint protection, firewalls, and email security, and gives full visibility at DNS level. It is often the only layer protecting devices that cannot run antivirus software, such as office printers, smart TVs, and guest Wi-Fi networks.
Tip: Discover practical ways to configure your DNS rules to boost productivity and block the specific ransomware and phishing threats that target small businesses.

Business VPN: Windscribe
Remote access remains a key topic for businesses in 2026 and beyond. A business-grade virtual private network gives you encrypted tunnels to manage secure access and prevent ISP snooping.
Windscribe meets the security needs for small businesses, such as securing remote workers and remote access. It offers centralized billing and team management, so you do not have to reimburse individual subscriptions. It gives remote workers a static IP if needed and secures digital assets accessed from public networks.
Tip: Sign up for Windscribe's Business VPN - Scribeforce for an all-in-one solution starting at only $3/user/month.
Identity and Password Management: 1Password
Identity is often the weakest link in a small business. If an attacker gets a valid password, firewalls and antivirus software might not spot it until it is too late. 1Password solves this by generating unique, complex credentials for every account and storing them in encrypted vaults.
It works well for small teams because it replaces the risky habit of sharing passwords via email or spreadsheets. You can create shared vaults for specific departments—like marketing or finance—so employees only access what they need.
1Password also includes Watchtower, a feature that alerts you if any company passwords are weak, reused, or appear in a known data breach. This gives you a clear view of your credential security without needing a complex audit. If an employee leaves, you can revoke their access instantly with a single click, keeping your business accounts safe.
Best Practice: Combine 1Password with MFA. Use 1Password to store the complex login, and use an authenticator app (or hardware key) as the second layer of defense.
Endpoint Security: CrowdStrike Falcon Go

For a long time, CrowdStrike was seen as a tool only for large enterprises. With Falcon Go, they introduced a bundle specifically for small and medium businesses that need top-tier protection without the high price tag.
It works well for small teams because it runs 100% in the cloud. You do not need to install heavy local servers or manage complex updates. It installs in seconds and uses AI to automatically block ransomware and malware. Falcon Go also includes device control, which helps you manage USB devices—a common entry point for malware in smaller offices.
The pricing for this tier is far more accessible than the enterprise versions, making it a realistic option for business owners who want the same technology protecting the Fortune 500, scaled down to fit their budget.
Firewall: Fortinet FortiGate
If you have a physical office, Fortinet FortiGate offers strong network security. These appliances combine firewalling, intrusion prevention, and web filtering in one box. Fortinet is known for high performance and strong threat detection. It integrates well with other security tools and provides a solid perimeter defence for protected devices inside your building.
For many businesses that work with managed service providers, FortiGate is a common choice, which can make support easier.
Vulnerability Management: Tenable Nessus
To find weak points, Tenable Nessus remains the industry standard. It scans your servers and workstations to identify missing patches and bad configurations.
For a specific business that holds highly sensitive data, running regular scans with Nessus ensures you stay a step ahead of attackers. It helps you prioritize which updates matter most, so you use your limited resources on the biggest risks.
Email and Collaboration Security: Microsoft Defender for Office 365
Many businesses already use Microsoft 365 for mail and files, so it makes sense to use the security tools that sit next to those accounts. Microsoft Defender for Office 365 scans links and attachments, filters phishing messages, and gives reports you can share with your team.
You turn it on in the same admin space you use for mail and user accounts, which keeps small business security simpler for one employee who looks after its operations. If your staff use Google Workspace instead, a similar setup with its built-in spam and phishing filters gives you the same kind of protection for email and shared files.
Bringing it Together: A Simple Security Program
You do not need to buy everything at once. A practical security program for SMBs starts with the basics:
- Identity: Turn on MFA for email and use a password manager to keep unique passwords for each account. Consider a tool that offers dark web monitoring to alert you if credentials leak.
- Network: Use Control D to stop threats at the DNS layer and gain full visibility into traffic. Pair it with clear security policies so staff know how to handle personal devices and access from home.
- Endpoints: Install CrowdStrike Falcon Go on all laptops and other endpoints as needed.
- Remote Access: Use Windscribe to protect remote work connections and give safe access to internal systems.
- Human Layer: Run regular employee training. Staff need to know how to handle new security challenges and spot phishing, so your cybersecurity efforts do not rely only on tools.
This mix protects your digital assets and keeps your security needs manageable. By focusing on these core cybersecurity tools, you reduce cybersecurity risk significantly without breaking the bank.
FAQs: Cybersecurity for Small Businesses
Which Cyber Security Tools Are Best For Business?
For most small and medium businesses, a strong base looks like this: MFA, a password manager with unique passwords, endpoint protection or antivirus software, DNS filtering such as Control D, email security, backup, and a virtual private network for remote access. Those cybersecurity tools give broad protection for common cyber threats without overwhelming their operations.
What is the 90/10 Rule in Cyber Security?
The 90 10 rule says roughly 10% of security comes from technology and 90% comes from people and process. In practice, that means cybersecurity software for small businesses only works when you back it with clear security policies, employee training, and simple checks on how employees handle sensitive data, login credentials, and access to business systems.
Does a Small Business Need Cyber Security?
Yes. Small business owners face the same modern threats as large firms, including data breaches and ransomware attacks. One weak account or exposed device can put business data, digital assets, and even cash flow at risk. A focused security program with a few well-chosen cybersecurity tools protects sensitive information and keeps your business running when new threats appear.

